Feature Focus: The macOS & Linux Client User Interfaces
Dive into the details of the Admin By Request macOS & Linux Client interfaces - the first thing your end users will see and interact with after installation.
Dive into the details of the Admin By Request macOS & Linux Client interfaces - the first thing your end users will see and interact with after installation.
Recent ransomware attacks on hospitals in Romania highlight the urgent need for healthcare organizations worldwide to strengthen their cybersecurity posture. With patient data at risk, proactive defense strategies are vital to safeguarding critical healthcare services.
Dive into the details of the Admin By Request Windows Client interface - the first thing your end users will see and interact with after installation.
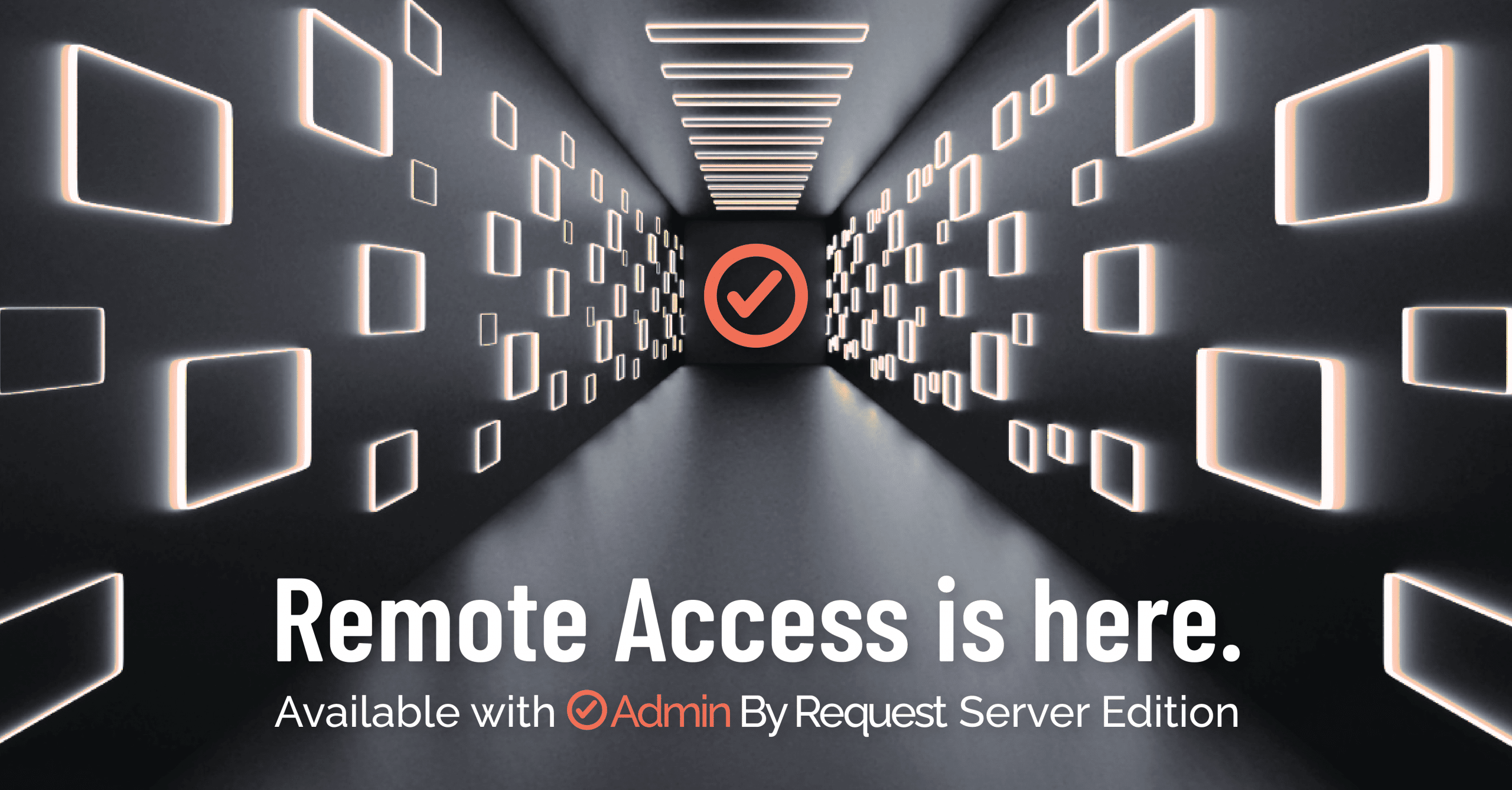
Explore the vulnerabilities exposed by the Ivanti VPN incident and discover why Admin By Request's Remote Access offers a superior alternative in the era of remote work.
Admin By Request has been recognized in Software Advice's 2023 FrontRunner’s Report thanks to its Machine Learning capabilities.
It's official... 𝗦𝗲𝗰𝘂𝗿𝗲 𝗥𝗲𝗺𝗼𝘁𝗲 𝗔𝗰𝗰𝗲𝘀𝘀 𝗵𝗮𝘀 𝗮𝗿𝗿𝗶𝘃𝗲𝗱 to the Admin By Request product suite! 🛡️🖥️🔒 That's right: you can now leverage familiar Admin By Request approval flows and features to enable secure,…
In IT, 'Nitro Boost' equates to local admin rights, offering a swift digital pace. Yet, like motorsports, it poses risks. EPAM emerges as a solution, ensuring security without compromising efficiency.
Think of local admin rights as like having keys to your house, or a keycard to a restricted area in your establishment – just like a regular set of keys, local admin rights provide access and control.
Ensure every endpoint in a mixed IT environment is covered by a single comprehensive Privileged Access Management tool with our latest release for Linux.
Every organization - large and small - should adopt a heightened posture when it comes to cybersecurity and protect their most critical assets against disruptive cyber incidents.
A July 4th ransomware attack by SafePay crippled Ingram Micro systems. Explore the breach, its impact, and the rising threat of supply chain attacks.
When security feels like punishment, users push back. Learn how invisible security and smart UX make compliance effortless and effective.
Removing admin rights doesn’t mean losing productivity. See how just-in-time elevation keeps users moving while IT regains control and cuts tickets.