Solutions
Security in
The SDLC
The Development Process
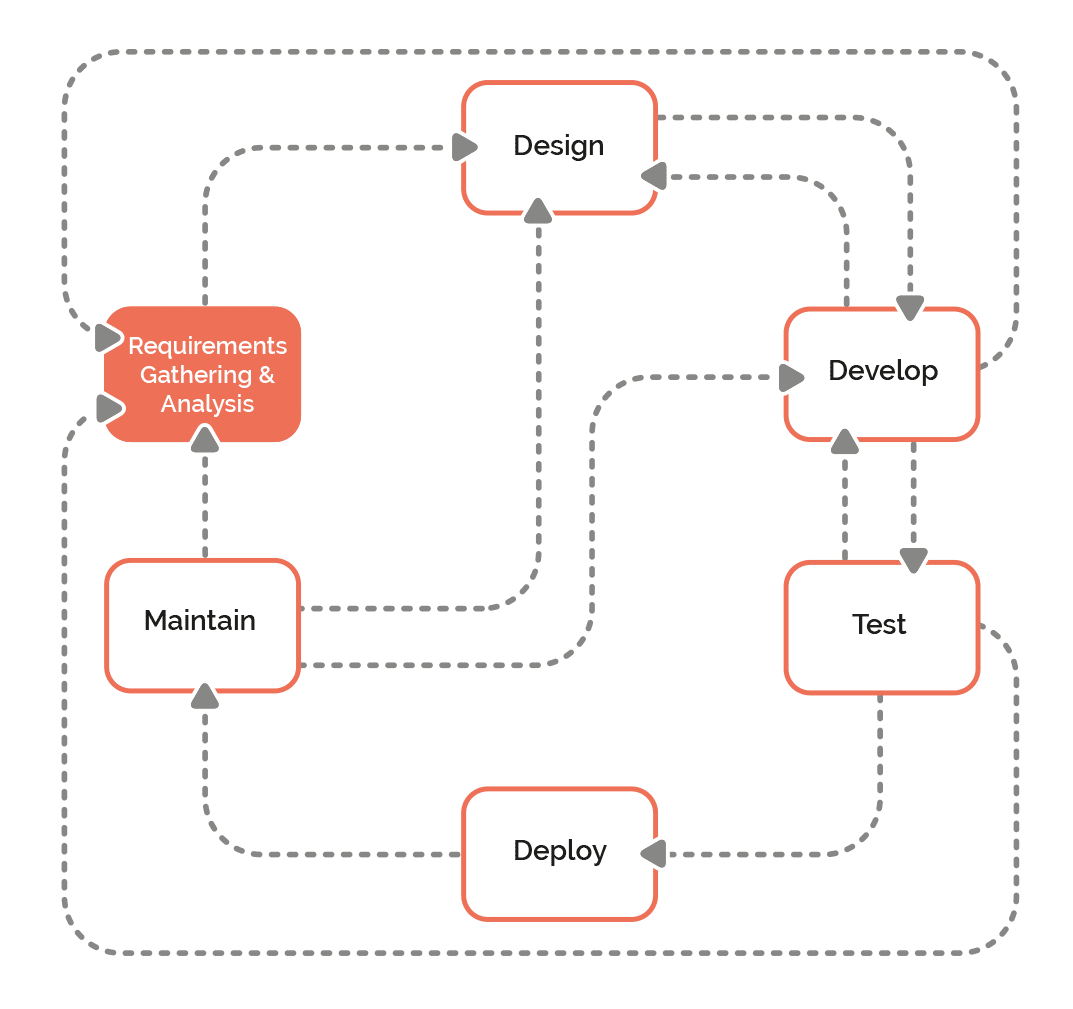
Overview
Software development at FastTrack Software follows a defined process intended to reduce the risk of project failure through the application of fast, iterative solution delivery, with continual testing throughout.
Methodology
This approach focusses on the benefits of a combination of two software development models, DevOps and Lean, to improve the delivery of both major projects and minor software updates.
Process
The diagram to the left provides an overview of the end-to-end process for software and feature development at FastTrack Software.

Management
There are three key areas of management in our software development process to ensure suitable coding practices are followed throughout, all processes are carried out effectively, the appropriate tests are conducted, and all changes are analyzed for impact prior to implementation.
Security Maintenance
After release, penetration tests are conducted both on endpoints and the system backend, including testing of source code and review of APIs to identify any security vulnerabilities. These tests are conducted annually, with a full report including the scope of the test available to customers in the Trust Center.
Vulnerability scans are conducted regularly using a series of known external scanners to test for security weaknesses in software systems. Results are generated by industry-standard providers Security Scorecard, Intruder, and Pentest-Tools, and others. Vulnerability scan reports are generated annually and are available to the public in the Admin By Request Trust Center.

Vulnerability Mitigation
We use a simple four-step Threat Modelling approach which integrates OWASP guidelines and various security threat perspectives (STRIDE and DREAD).

