Discover Our Core Features
The tools you need to empower your team, reduce helpdesk tickets, streamline workflows, and simplify compliance
One Powerful Platform To Solve Multiple Problems
Product Key:
Endpoint Privilege Management
Secure Remote Access
Boost Productivity
Run as Admin
Admin Session
PIN code
Pre-approval
Application blocking
Automate & Streamline
AI auto-approval
Machine Learning
IdP integration
Clean Up Local Admins
Unattended Access Discovery Module
Lock Down Security
Break Glass/LAPS
Device Owner
Just-in-time elevation
Malware scanning (37+ engines)
Tamper prevention
Support Your Team
Remote support
Screen sharing and control
Multi-monitor support
Controlled vendor access
Mobile application
Simplify Compliance
Full audit logging
Session recording
MFA/SSO endpoint enforcement
Reason tracking
Granular privacy
ALL AVAILABLE WITH OUR LIFETIME FREE PLAN
25 Seats, All Core Features, No Strings Attached
Learn More About Our Core Features
For PDF guides, technical specifications, and detailed feature breakdowns visit our Documentation Center
Boost Productivity

Run As Admin
Elevate individual applications, not entire user sessions.
Users can run a single application with elevated privileges, without gaining system-wide admin rights. Only that specific process has administrator rights, not the user.
Perfect for everyday tasks like installing approved software or running trusted tools. The session lasts only for the duration of the install and applies only to that particular application.
- Requires approval from IT before elevation
- Requires a reason for audit logging
- Pre-approve trusted applications to eliminate friction
- Block specific applications from ever being elevated


Admin Session
Time-bound system-wide access for complex tasks.
For tasks that require broader permissions, like installing drivers or changing system settings, users can request a protected administrator session. They become temporary members of the local administrators group for a configurable period (default 15 minutes).
Even with full access, users cannot uninstall Admin By Request or modify user accounts. All activity during the session is fully audited, including the reason provided, anything installed, and any applications executed.
Any files downloaded are run through 37+ anti-malware engines before running on the endpoint, made possible through integration with OPSWAT’s MetaDefender Cloud API.
Sessions automatically terminate when the timer expires or the user logs out, whichever comes first. See Admin Session documentation.


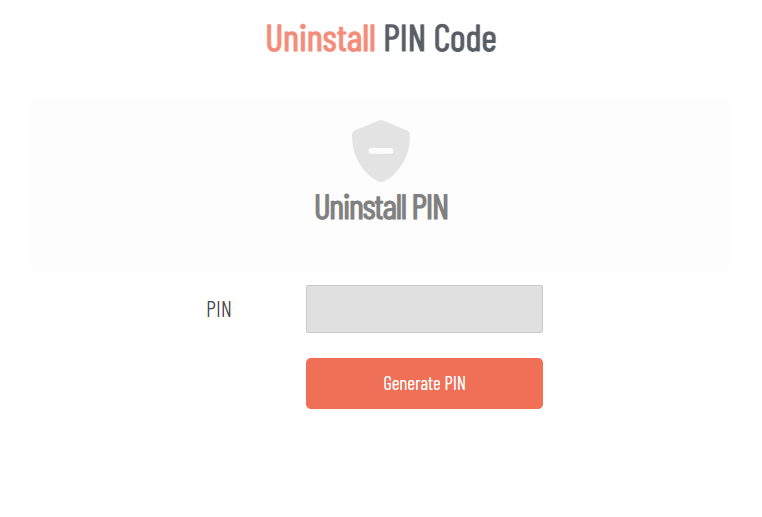
PIN Code
Admin By Request provides two PIN Code functions to handle situations where standard workflows aren’t available.
For offline or out-of-scope elevation, the dual-PIN system enables users to gain administrative privileges when they can’t connect to the portal for approval. This is particularly useful when Require Approval is enabled but the endpoint has no internet connection, or when users outside the normal scope of permitted users need to perform occasional administrative tasks like printer installation. The end user generates one PIN while an IT administrator generates another from the portal. When both codes are entered together into the Admin By Request popup window, elevation is granted.
For uninstallation, IT administrators can generate a one-time PIN code from the portal that allows local removal of Admin By Request from a device. This is valuable for offline endpoints, field devices, or any situation where standard remote management tools aren’t accessible. Once generated, the PIN works only once, maintaining security while providing flexibility for device management outside the network.
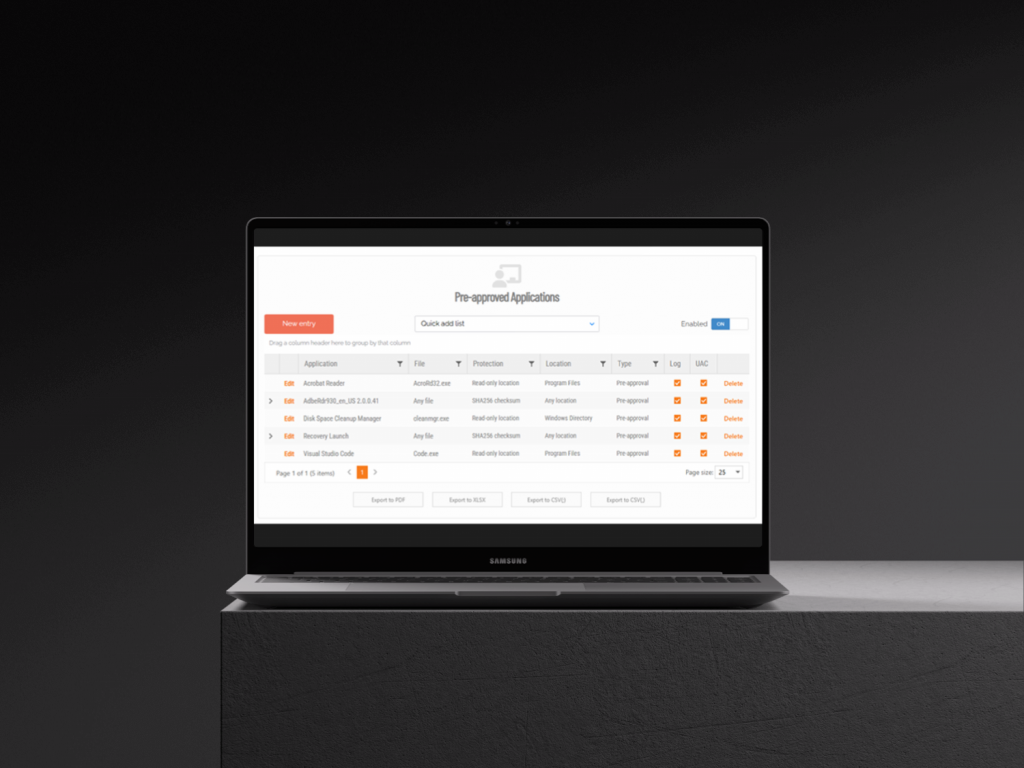

Application Pre-approval
Bypass approval workflows for trusted applications without granting full admin rights.
Some legacy tools or department-specific software need to regularly run elevated. Rather than processing repetitive approval requests for the same trusted programs, or giving users permanent local admin access, you can pre-approve specific applications. Users can then run these programs with elevated privileges automatically, without gaining full system-wide admin rights or waiting for IT approval.
Pre-approval works globally or can be scoped to specific groups through sub settings. For example, if your engineering department needs a specialized tool, you can add it to the engineering sub setting’s pre-approved list. Only that department will be able to auto-elevate the application, while it remains restricted for everyone else. This granular, controlled whitelisting eliminates the workflow burden for routine, trusted applications while maintaining security boundaries across different user groups and departments.

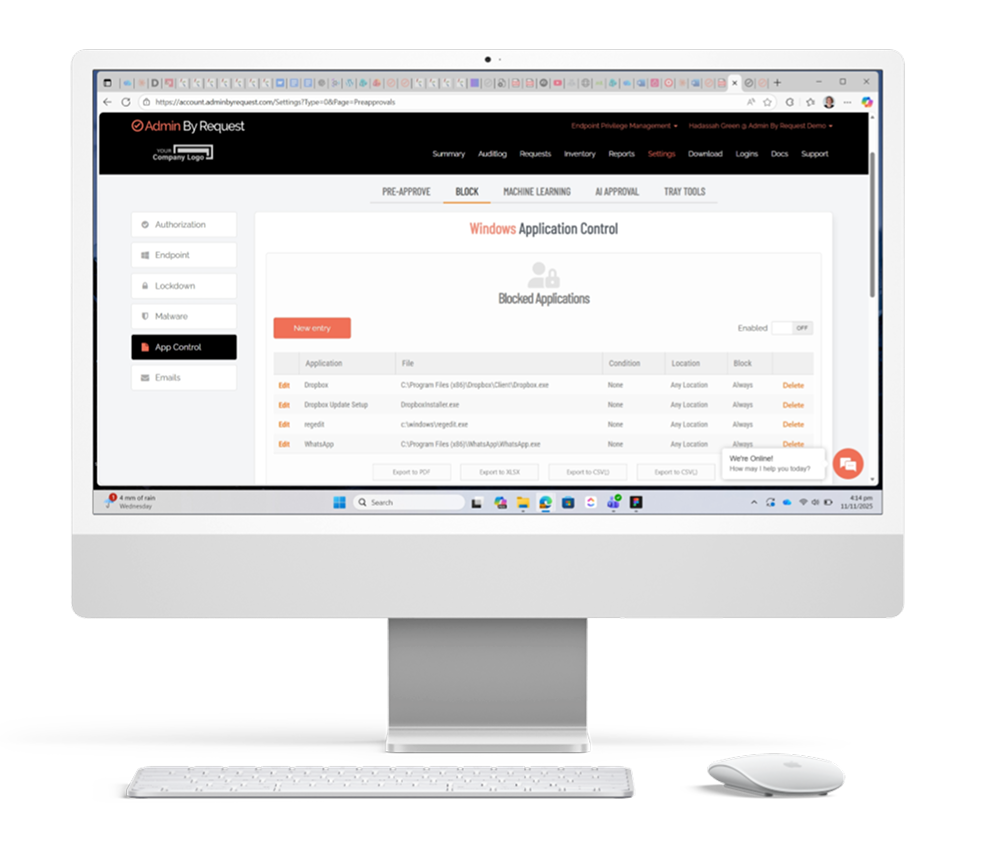
Application Blocking
Prevent unauthorized or malicious software from running with elevated privileges.
Not every application should be allowed to run with administrative rights. Application blocking lets you specify programs that users cannot execute with elevated privileges, protecting your environment from known malicious software, unauthorized tools, or risky applications. You can block based on file name, checksum, vendor, or file location.
For maximum security, blocking by checksum or vendor is recommended. Blocking solely by file name is strongly discouraged because users can easily bypass it by renaming the file. By using more robust identifiers like checksums (which verify the exact file contents) or vendor certificates, you ensure that blocked applications stay blocked regardless of how they’re renamed or where they’re stored.
Keep dangerous or policy-violating software locked down, even when users attempt to circumvent restrictions.
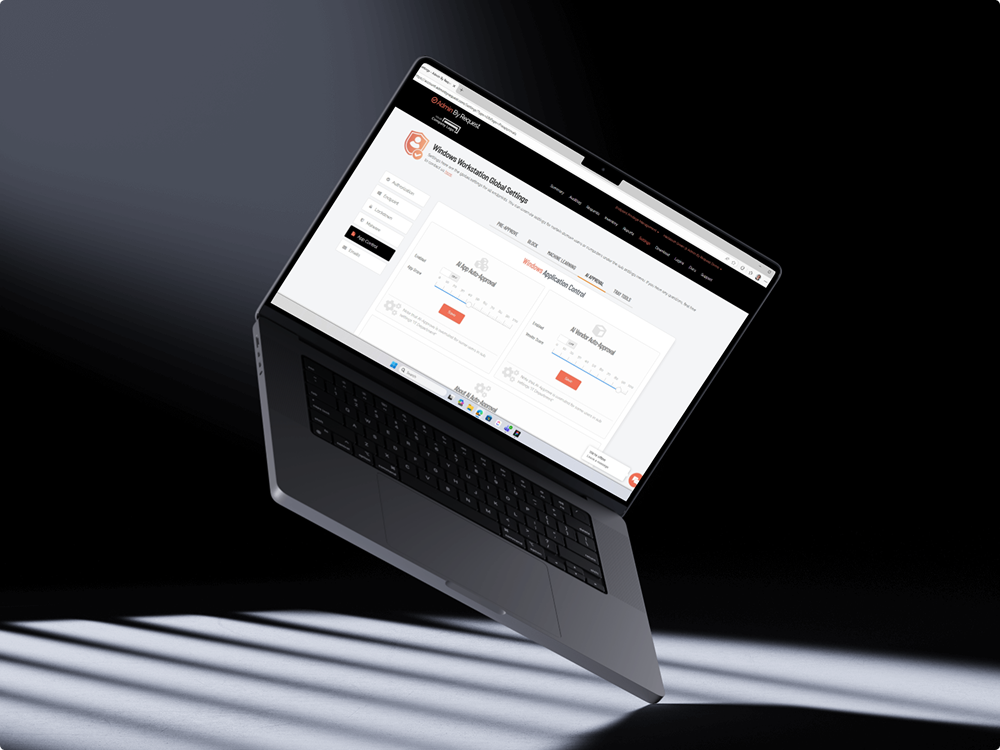
Automate and Streamline

AI Auto-Approval
Intelligent automation for common applications based on popularity and trust scores.
Admin By Request analyzes elevation requests across its customer base to identify which applications are commonly run with elevated privileges. Each application receives two scores between 0 and 100%, measuring both the application’s popularity and its vendor’s reputation. Well-known applications from reputable vendors like Microsoft Office score at the higher end of the scale, while rarely used software from unknown vendors receives low scores.
Organizations set their own threshold score, based on their individual risk tolerance. Any application meeting or exceeding that threshold gets automatically approved by the AI engine. Very low scores (0-1) flag applications from unknown vendors that carry higher risk and should be reviewed manually on a case-by-case basis.
The result is reduced approval burden on IT teams without compromising security. See AI Approval documentation.

Machine Learning
Build your pre-approved list automatically based on IT approval patterns.
When an IT administrator approves an elevation request, they’re signaling that the application is safe to run. If the same application gets approved multiple times, it’s a clear indication that it belongs on your pre-approved list. Machine Learning Auto-Approval recognizes this pattern and automates the process.
You set a threshold for how many times an application needs to be manually approved before the system adds it to the auto-approved list. Once an application reaches that number, it’s automatically approved for all future requests. This approach builds your pre-approved list organically as your employees use software in their daily work, eliminating repetitive approval tasks for IT while ensuring only vetted applications make the cut.
The system learns from your actual approval decisions rather than requiring you to anticipate every application your organization might need. See Machine Learning Documentation.

IdP Integration
Admin By Request integrates with major identity providers to simplify portal access and policy management.
Single sign-on (SSO) is supported for all common identity providers, either directly or through generic SAML 2.0, including ADFS and Azure AD. This eliminates separate credentials for the Admin By Request portal and leverages your existing authentication infrastructure.
Beyond SSO, identity provider connectors pull group information from Entra ID (formerly Azure AD), Google Identity, JumpCloud, and Okta to power Sub-Settings. These connectors retrieve your existing user and device groups, allowing you to apply different privilege policies to specific departments, teams, or organizational units without recreating group structures. For Azure AD environments, provisioning support automatically syncs user identities and access changes from your IdP to the Admin By Request portal during each provisioning cycle, keeping user management centralized in your identity platform. Visit The Integration Hub.

Clean Up Local Admins
Automatic removal of unnecessary administrative privileges.
Admin By Request automatically downgrades users from Admin to Standard User when they log on, eliminating the need to manually manage local administrator accounts across your endpoints. This ensures that users maintain standard permissions unless they explicitly request elevated access for specific tasks.
Administrators can exclude specific accounts from revocation when necessary, maintaining flexibility for service accounts or other exceptions. Tamper-prevention mechanisms prevent users from reinstating their own admin rights during active sessions.
When users need temporary elevated access, they can request it through Just-In-Time features like “Run As Admin” for individual applications or “Admin Session” for broader system access. See Clean-up Local Admins documentation. See Clean-up Local Admins Documentation.

Unattended Access Discovery Module
Automatic discovery of network-connected devices.
The Discovery Module automatically scans your network to identify all connected endpoints and reports findings back to the portal about devices responding on standard remote access ports (RDP on 3389, SSH on 22, and VNC on 5900/5901). This enables IT administrators to discover and connect to agent-less devices like routers, firewalls, and other network infrastructure that wouldn’t otherwise appear in your inventory.
By providing visibility into all remotely accessible devices across your network, the Discovery Module eliminates manual asset tracking and ensures no endpoints slip through security oversight. When deployed as part of an on-premise gateway setup, it integrates seamlessly with your existing infrastructure while maintaining full control over network scanning and device access.
Lock Down Security

Break glass/LAPS
One-time local admin accounts when everything else fails.
Domain trust broken? Need to grant a consultant temporary server access? Break Glass provisions secure, temporary local administrator accounts for emergency situations.
Unlike Microsoft LAPS, credentials are randomly generated, stored encrypted (never in plain text), and work only once. Accounts must be used within one hour and expire automatically. For Windows 8.4+, accounts take effect instantly with no reboot required.
This is emergency access done right: secure, auditable, and impossible to extend or reuse. See Break Glass/LAPS Documentation.


Device Owner
Restrict administrative access to designated device users.
The Device Owner feature allows you to lock down elevation privileges to a single user. The first non-administrator to log on to a device automatically becomes the Device Owner, with their identity tracked in your inventory and reports for centralized visibility.
Once assigned, you can restrict “Run As Admin” and “Admin Session” to only the Device Owner, preventing other users from gaining elevated access. This is especially valuable with lenient elevation policies, ensuring only the primary user can request administrative rights.
Administrators can view, reassign, or release device ownership as needed, putting complete control in your hands to balance security with productivity. See Device Owner Documentation.


Just-in-Time Elevation
Privileges granted only when needed, minimizing attack windows.
Rather than allowing users to maintain constant administrative rights, Admin By Request grants elevated privileges only when users actually need them. Users can request elevation for a single application through “Run As Admin,” which sandboxes elevated permissions to just that process, or request a protected “Admin Session” for broader system-wide access when tasks require wider permissions.
Both elevation methods are time-bound and fully audited, so you see in detail who requested access, why they needed it, and what they did while elevated. Sessions automatically terminate when the timer expires or the user logs out. This approach dramatically reduces the attack window by ensuring users spend minimal time with elevated rights, significantly decreasing the risk of account compromise or lateral movement by attackers.




Malware Scanning
Real-time protection against malware before elevated execution.
Whenever a user attempts to run a file with administrative privileges, Admin By Request automatically scans it using OPSWAT’s MetaDefender service, which employs 30+ commercial antivirus and anti-malware engines. This multi-engine approach delivers over 99% detection rates for known threats and catches zero-day exploits that individual antivirus products miss.
The checksum-based lookup happens instantly against MetaDefender’s global database of 40+ billion file signatures, and takes less than 0.1 seconds with no performance impact. Malicious files are blocked immediately before execution. Unknown files can optionally be sent for cloud scanning.
This transparent protection lets you confidently allow elevation requests without requiring individual approval, knowing malware scanning is automatic and always active. See Malware Scanning documentation.


Tamper Prevention
Multi-layered protection against unauthorized modifications.
During administrative sessions, Admin By Request continuously monitors all important system files to prevent unauthorized changes. Users cannot add, modify, or delete user accounts, nor can they uninstall Admin By Request itself. Attempts to alter protected files are immediately blocked, restored to their original state, and logged for audit review.
The system also detects clock changes and immediately terminates the session if tampering is detected, preventing users from extending their elevated access beyond the configured time limit. These layered protections ensure that even when users have elevated privileges, they cannot compromise the security infrastructure or extend their access without detection, maintaining control and visibility at all times.

Support Your Team


Remote Support
Secure, just-in-time remote assistance for distributed teams.
Remote Support enables IT administrators and end users to initiate secure remote sessions for troubleshooting and support without requiring traditional VPN or RDP access. Sessions are established through secure Cloudflare Tunnels and just-in-time VNC servers, providing immediate assistance to remote and hybrid workers while maintaining security controls.
Both admin-initiated and user-initiated support requests create audited records of who accessed what and when. Session recording captures the entire interaction for compliance verification and quality assurance. For remote workforces, this eliminates delays in getting support while ensuring that all support activity is logged and can be reviewed. The ability to set maximum session durations prevents support sessions from running indefinitely, maintaining control over remote access.

Screen Sharing and Control
Enable productivity without compromising security.
Admin By Request Remote Support includes screen sharing and remote control capabilities, allowing support staff to see what users are experiencing and take control when necessary to resolve issues quickly. A “View Only” option lets administrators observe without controlling, useful for sensitive environments or when users prefer to retain control.
Either party can hide the screen from the remote person, giving users privacy control during support sessions. Screen recording is automatic, creating an audit trail of all support activities for compliance frameworks like SOC 2 and HIPAA. MFA can be required for portal users initiating sessions, ensuring only authorized personnel can connect. These controls allow you to provide efficient support to distributed teams without sacrificing security or audit visibility.


Multi-Monitor Support
Full visibility across complex remote environments.
For users with multiple monitors, Remote Support clearly displays which monitor is being viewed and allows easy switching between them. This eliminates confusion during remote troubleshooting and ensures support staff can fully understand the user’s environment and resolve issues more efficiently.
For hybrid workforces with varying setups, multi-monitor support reduces support call duration and improves first-contact resolution rates. Users don’t need to describe which screen they’re working on, and support staff can quickly navigate the entire desktop environment.
This combination of visibility and functionality means faster issue resolution without requiring the user to spend time explaining their setup.


Controlled Vendor Access
Secure third-party access without sacrificing control.
Vendor Access allows external users to access internal devices through a web browser without installing additional software, using the same secure infrastructure as other Admin By Request remote access features. Access is controlled through Portal User Logins where administrators define scopes to limit what resources vendors can access, including specific computer types, OUs, groups, or domains.
Vendors access resources through a dedicated portal (access.work) with SSO required for enhanced security. All vendor sessions are fully audited and can be recorded for compliance verification. A “Limit to access.work” setting prevents vendor users from accessing your main Admin Portal. This controlled approach allows you to work securely with third-party vendors and consultants while maintaining complete visibility and control over what they can access and ensuring compliance requirements are met.
Simplify Compliance


Full Audit Logging
Complete visibility into all privileged access and activity.
Every administrative action is recorded in a centralized audit log with full details including user identity, device, what was executed, session duration, and more. This applies equally to endpoint privilege management actions like application elevations and admin sessions, as well as secure remote access sessions for both IT support and vendor access.
A unified audit log across both capabilities provides comprehensive visibility into who did what and when across your entire infrastructure. This is essential for compliance frameworks like SOC 2, HIPAA, and PCI-DSS, which require proof of access controls and activity monitoring. Detailed audit trails enable rapid incident investigation, ensure accountability, and provide the documentation needed for compliance audits and incident response.


Session Recording
Replay remote sessions for security and compliance verification.
Admin By Request automatically records video of all Remote Support and Vendor Access sessions, allowing administrators to replay sessions for training, quality assurance, and security verification. This is particularly valuable for remote and hybrid workforces where visual confirmation of remote work activity strengthens security posture.
Recorded sessions are stored securely and linked to your audit log, creating a complete record of who accessed what resources and exactly what they did. Many compliance standards require this level of documentation, making session recording an invaluable tool for meeting regulatory requirements while maintaining visibility over distributed teams.


MFA/SSO Endpoint Enforcement
Multi-layered authentication across all privileged access.
Admin By Request can require multi-factor authentication for administrators accessing the portal, requesting privilege elevation, and initiating remote sessions. SSO integration can be mandated for users accessing remote resources and for elevation requests. These authentication layers protect against unauthorized access even if credentials are compromised.
For distributed teams, MFA and SSO provide secure access from anywhere while simplifying credential management across your organization. They apply consistently to both endpoint privilege management and secure remote access, ensuring that only verified users can perform administrative actions or access sensitive resources. They’re also standard requirements for compliance frameworks and security policies. See MFA documentation.


Reason Tracking
Documentation of why administrative access was needed.
When users request administrative elevation or remote access, they can be required to provide a reason for their request. These reasons are captured and stored in the audit log, creating a complete record of not just what was done, but why it was necessary.
Reason tracking ensures accountability across your entire privileged access infrastructure and provides context for investigating unusual activity. It supports compliance by documenting the business justification for privileged access, demonstrating that both elevation requests and remote access follow proper authorization procedures.
For teams where direct oversight isn’t possible, this creates transparency and accountability.

Code of Conduct
Customizable notification of monitoring and security policies.
Before granting administrative access, whether through endpoint privilege management or secure remote access, Admin By Request displays a customizable Code of Conduct page. This explains your organization’s security policies, monitoring practices, and acceptable use expectations, setting clear expectations with users and ensuring they understand their actions are being audited.
The Code of Conduct applies consistently across all privileged access scenarios, from local admin sessions to remote support sessions. For remote and hybrid teams, it provides transparent communication about monitoring without requiring in-person discussions, helping ensure compliance with company policies across geographically distributed workforces. It also supports legal compliance by documenting user acknowledgment of monitoring practices.

Ready To Make Compliance Simple?
Try our free plan with all core features and 25 Seats, or book a free 30-minute demo with one of our experts
Security Without Compromise
Free Plan
What You’ll Get
All core features
25 Endpoint Privilege Management Seats
25 Secure Remote Access Seats
Lifetime Free
Unattended Access
‘All You Can Eat’ Features
No confusing pricing tiers
No hidden fees, paid add-ons, or modules
No. of seats + term length = price
ALL features and support included in Enterprise plan
Price on Request
Vendor Access
What You’ll Get
All core features
Scalable Endpoint Privilege Management seats (50+)
Scalable Secure Remote Access seats (50+)
Full support and training
Time-limited access grants





