There aren’t many live sports being broadcast for our entertainment on television at the moment, thanks to (you guessed it) Covid-19.
But ransomware operators are doing their best to pick up the slack in this area, providing a merciless boxing-like performance of hit after hit on organisations – with the latest victim being our ‘Old Time’ friend, Jack Daniel’s.
A Heavyweight Opponent: REvil
The ransomware responsible for this foul play is called REvil (also known as ‘Sodinokibi’ or just ‘Sodin’) and certainly isn’t pulling any punches in the relentless bout of Ransomware vs. The People.
REvil is thought to be the improved and more exclusive version of GandCrab, a similar piece of ransomware that earned a killing for its developers who made use of the ransomware-as-a-service (RaaS) model.
The belief that the two are related stems from the strong similarities in the code, the URL building logic, the infection process of the ransomware and the RaaS business model tactic, as well as the suspiciously coincidental fact that the GangCrab crew announced their retirement at the same time that REvil picked up the pace.
The danger here is that GandCrab were highly successful, gaining notoriety for holding a 40% share of the ransomware market as of February 2019, according to Bitdefender.
So if the GandCrab gang are in REvil’s corner, the likes of Jack Daniel’s can expect to face a GandCrab-level challenge from REvil – which is exactly what appears to be happening.
Attackers are Aiming Below the Belt
When it comes to organisations that have been jabbed, hooked and sucker punched by REvil, the list is long, including currency exchange business Travelex and law firm Grubman Shire Meiselas & Sack.
But the most recent victim, Brown-Forman, is in the food and beverage industry – a sector that has already been hit hard by Covid-19 as recreational activities and luxuries like alcohol and spirits take a back seat.
In August 2020 REvil ransomware reportedly infiltrated the organisation’s system and exfiltrated data for a month, claiming to now have 1 Terabyte of the company’s data dating back to 2009 – claims which they have backed up with screenshots.
JD’s parent company hasn’t provided much detail about the attack but have confirmed that data was stolen. However, they did manage to prevent the ransomware from encrypting any files and are not negotiating with the cyber gang responsible.
But as promised, REvil is showing no mercy, now threatening to auction the stolen data off to the highest bidder on their dedicated leak site in an attempt to force payment from old Jack and his team.
In true cyber criminal fashion, the attackers have no qualms with kicking an organisation when they’re already out for the count.
Ransomware-as-a-Service: A Blow-by-Blow
The RaaS model takes after its namesake, SaaS (software-as-a-service).
Cyber gangs essentially act as vendors, selling or renting out advanced ransomware kits or services on the dark web to other cyber criminals who may not have the skills to create or launch advanced ransomware programs by themselves.
Cyber criminals who purchase the software become affiliates of the ransomware vendor. They can then launch malware attacks on victims of their choice using the purchased or rented malware, or, in some cases, get the ransomware provider to do it for them.
Affiliates typically charge a ransom when they launch attacks, and any payments made by victims are split between the affiliate and the RaaS vendor, depending on the arrangement or contract between the two parties.
As RaaS, REvil is spread in any way that its distributors see fit, be that via Remote Desktop Protocols (RDPs), spam and phishing campaigns and insecure Virtual Private Network connections (VPNs), to name the most common.
RaaS is a fearsome new tactic because advanced attacks, such as REvil, can come from a number of affiliates rather than from the single cyber gang who created the malware. You can also guarantee that ransomware as popular on the dark web as REvil certainly does a good job at what it was created for.
The RaaS business model is being implemented increasingly by ransomware developers because it’s a win-win: they get their product purchased and distributed by a large network of partners and then reap the rewards from every successful attack.
Malware Breakdown: A Lethal Combination
A threat analysis completed by Secureworks demonstrates how much body work REvil does to ensure these attacks are successful.
Its tactics include:
- Exploiting what is known as the CVE-2018-8453 Windows vulnerability, which allows an attacker to gain the highest level of privileges on a host device.
- Prompting users to run a sample of the malware as administrator in the case of REvil being unsuccessful in exploiting the CVE-2018-8453 vulnerability.
- Checking that the target device is not whitelisted. The ransomware comes with a list of countries that are whitelisted from being attacked by REvil and its distributors.
- Terminating specific services and processes prior to performing encryption.
- Deleting shadow volume copies (backup copies or snapshots of computer files or volumes).
- Whitelisting certain files and folders from being encrypted.
- Encrypting non-whitelisted files and folders both on the local device storage and within shared network spaces.
- Exfiltrating encrypted data from the host device to the remote operators.
- Erasing the contents of blacklisted folders.
- Customizing the ransom note name, contents and background image.
And following in line with the RaaS model, affiliates can tailor and configure the ransomware to their own preferences – depending on who they target and how they want the malware to behave on the target environment.
Secureworks provides this graphic as part of their in-depth analysis of REvil’s attack combo, showing the core functionality of the ransomware and it’s execution process:
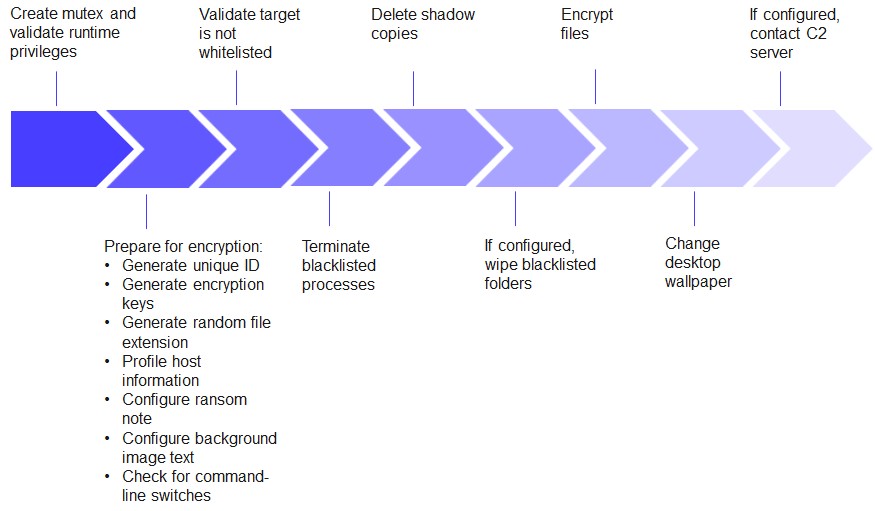
REvil execution flow. (Source: Secureworks)
Stay a Step Ahead of the Enemy: Know Their Weaknesses
There is a lot involved in REvil’s game plan, but our focus is on a key component that REvil bases its attack on: it always attempts to gain privileged access to the host device.
Once REvil has gained elevated privileges, it can then go about executing its long list of processes upon the victim and essentially take complete control of the infected system.
According to a breakdown by Intel471, REvil attempts to gain privileged access using one of two methods:
- The first is by exploiting the previously mentioned CVE-2018-8453 Windows vulnerability to gain system privileges.
- If the program cannot exploit the CVE-2018-8453 vulnerability, the second method used is persistently prompting the user to run a single sample of the ransomware as administrator, until the user gives in and agrees.
Once privileged access is gained, you may as well wait for the eight-count – it’s game over.
Get Admin By Request in Your Corner
Despite REvil’s advanced inner workings and (so far) lucrative RaaS business model, it would be a safe bet to say that software that can detect REvil within the IT system and also prevent it from gaining privileged access would be a pretty good contender against ransomware that requires privileged access to go the distance.
Admin By Request is a Privileged Management Access (PAM) solution that does just that.
PAM solutions manage privileged access by revoking user admin rights so that they only have the minimum privileges on their device to perform their function in the workplace – a practice termed the Principle of Least Privilege (POLP).
A comprehensive PAM solution also allows for Just-in-Time elevation (JIT), in which users can only gain elevated privileges when and where they need them.
Admin By Request implements POLP, JIT and anti-malware technology to throw more than a few counterpunches at ransomware such as REvil.
This security solution ensures that:
a) Privilege escalation cannot occur undetected.
b) Users cannot run anything as administrator without first gaining explicit permission from an IT admin.
c) All applications run with elevated privileges are scanned with OPSWAT MetaDefender’s 30+ malware detection engines.
Admin By Request manages user access by revoking user’s admin rights without making a scene or messing with any heads.
Every endpoint that has the software installed gets protection from privilege-seeking ransomware, without the need for re-education of users.
That’s because, to gain privileged access when they need it, users simply use one of the four intuitive methods of elevation provided by Admin By Request:
- Whitelisting / Pre-Approval: You decide what programs are safe to run with elevated access and pre-approve them for use.
- Run as Admin: Your users simply right click an application they want to run with admin rights, provide their email and phone number and a reason for making the request. You get the request immediately on your end and can either approve or deny it.
- Elevated Session: Following a similar process to Run as Admin, a Full Session Elevation requires a request from the user, along with their details and a reason for the request. If approved by you, that user can then have a timed session of admin access to their device.
- PIN Code: All of these elevation methods are set up by you within the Admin By Request user portal, where you can create groups and sub-settings determining which uses can do what. If a user can’t use one of the previous methods of elevation due to falling outside of the groups, settings or scope configured in your user portal, they can use a PIN code provided by an IT admin, to the same effect.
The Auditlog within the Admin By Request user portal records all activity undertaken when a user has elevated access, making it extremely difficult for a user – or ransomware – to climb the ranks of privilege without you knowing about it.
This means you can detect and prevent unauthorized privilege escalation before that bell rings – this time it’s REvil’s turn to tap out.
Saved by the PAM
So don’t throw in the towel just yet – because cyber criminals certainly won’t be.
As much as it feels like Jack Daniel’s and other targeted companies are the underdogs in the ever-increasing RaaS ransomware faceoffs, there are solutions that ensure organisations can go toe-to-toe against heavyweights like REvil.
Admin By Request is one of these solutions. Get in touch with us or download our free plan before it’s you who ends up in the ring facing the next formidable ransomware opponent.







