The ‘unprecedented year’ of lockdowns in 2020 saw a huge percentage of workforces go remote, and for many organizations, working from home (WFH) is still the norm in 2021.
The past 24 months resemble something of a rollercoaster: the scramble to transition hundreds of employees to a remote workforce, the struggle to maintain productivity throughout the chaos, the panic at the loss of all cybersecurity policies and protections, the slow plugging of the many security holes left gaping wide as a result of the move, and finally a sort of nervous calm as the dust settled and things just barely started getting back to where they were pre-COVID.
Meanwhile, and here’s the kicker: cybercriminals have been sitting back, rubbing their hands, and watching it all unfold – while continuing to wreak havoc on their victims.
The Proof is in the Percentages
Verizon’s 2020 Data Breach Investigation Report (DBIR) provided some insight into just how unaffected cybercriminals were during the first of the two years that threw the world off balance:
Of the 32,002 security incidents investigated by the Verizon team, 3950 of these were confirmed breaches.
- 70% were perpetrated by external actors
- 55% were perpetrated by organized crime groups
- 45% involved hacking
- 86% were financially motivated
- 72% involved large businesses
The second year of COVID-calamity didn’t bring much reassurance, with Verizon’s latest report (2021 DBIR) shedding light on data breaches from a range of sources:
Of the 2021 data breaches investigated:
- 85% involved the human element
- 61% involved credentials
The following took out the number one spot in various data-breach categories:
- Top action used: Hacking, just under 40%
- Top threat actor: Organized crime, over 80%
- Top motive: Financial, over 70%
- Top data type sought-after: Credentials, just under 60%
- Top misuse variety: Privilege abuse, over %70
- Top attack vector for hacking attacks: Web Applications, over 90%
- Top hacking variety in Desktop-Sharing attacks: Use of stolen credentials or brute force, 89%
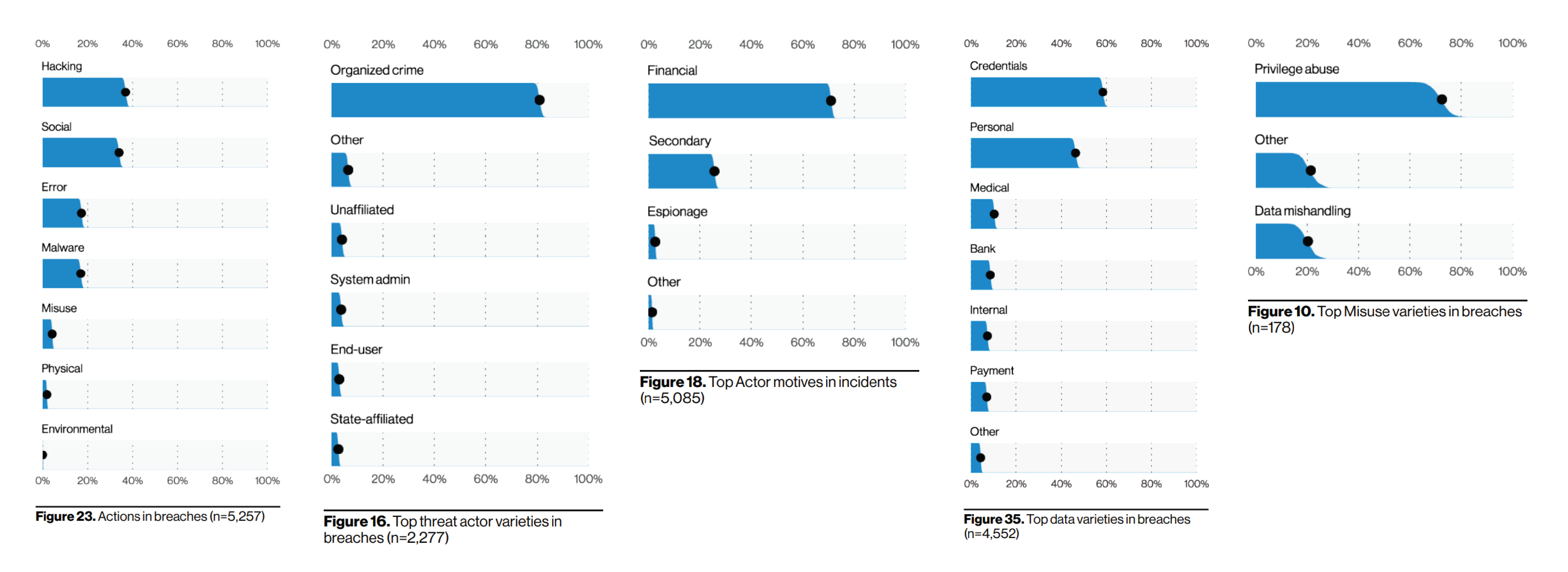
Verizon 2021 Data Breach Investigations Report (DBIR)
But we should hardly be surprised that 2021 only brought more bad news; in October 2021 the Identity Theft Resource Center (ITRC), who track publicly reported data breaches in the US, revealed that the number of data breaches to date (that is, three whole months before the end of the year) had already surpassed the total number reported for the entire year of 2020.
Interpreting the Integers
So how do we make sure 2022 doesn’t join it’s two predecessors in the hall of infamy?
Use the stats to plan a better defense.
An insightful Forbes commentary helped us put together some tips on what you can do.
1. Be more diligent with monitoring assets and devices.
Do you have full visibility of all of your company devices? Do you know their exact locations and current configurations?
According to Forbes, not having access to this information for all devices means complete protection cannot be guaranteed.
For every endpoint that isn’t sufficiently monitored, an attack surface exists – ripe and ready for exploitation by cybercriminals.
Monitoring every endpoint minimizes your organization’s threat surface.
2. Protect endpoints to prevent large-scale attacks.
A single, unprotected endpoint can be the foothold for a large-scale attack on an entire organization – and we know that cybercriminals do not shy away from large targets.
According to Verizon’s 2020 DBIR, the vast majority of security breaches targeted large businesses. In 2021, some of the biggest data breaches included:
- The Colonial Pipeline attack by DarkSide on one of America’s largest oil and gas companies, in which just under 100GB of data was stolen.
- The JBS Foods hack, in which JBS (employer to approximately 250,000 people) paid REvil an $11 million USD ransom in Bitcoin after their networks were compromised.
- CNA’s $40 million ransom. One of the US’s largest insurances companies paid the largest publicly known ransom of all time to Phoenix ransomware group – $40 million USD.
Three massive targets, three massive attacks, and some mind-boggling ransoms paid; all in 2021.
But these large targets are often compromised by small weaknesses, which frequently present themselves in the form of unprotected endpoints – endpoints that organized crime groups are relentless in scoping out.
Only one inadequately protected endpoint is required for a cybercriminal to wreak havoc among several thousand endpoints.
Forbes describes an ‘unbreakable digital tether’ connecting each of your endpoints as being key to ensuring the security of every device and the wider network.
3. Go cloud-based – the way of the future.
Many organizations have already made, or are in the process of making, the move to cloud-based operating, with WFH becoming the preferred, and often enforced, method in times of global pandemic.
As well as allowing organizations to provide a larger scale of applications for their remote workforce, cloud-based over on-premises operating comes with several cybersecurity benefits:
Cloud-based assets had a much lower rate of involvement in security breaches according to Forbes; 24% compared to 70% involvement for on-premises assets. These statistics suggest that you’re less likely to be targeted if you’re operating in the cloud.
Cloud-based endpoint security also provides a higher level of security, with real-time monitoring, analysis and alerting available to help prevent cyberattacks. If you need more convincing, cloud-based security solutions often come in much easier-to-deploy and cost-efficient packages than their on-premises counterparts.
4. Manage privileged access to shut down breach attempts.
According to the past two Verizon DBIRs, credential theft is one of the most common culprits in security breaches: of the percentage of breaches that saw hacking as a contributing factor, over 85% of these involved brute force or lost / stolen credentials.
This consolidates Credentials as the winner of the most sought-after data type in 2021.
The higher the privilege of a set of user credentials, the more valuable they are to hackers looking to exploit; local administrators can do much more on their device than regular users, such as make changes that affect other user accounts and the wider system and network.
For that reason, a single compromised endpoint that has administrator access is not a single compromised endpoint at all – instead, it can mean an entirely compromised network.
Because of this, managing privileged access on company devices is paramount.
If you have full visibility and control over who has administrator access and who doesn’t, and you can monitor any changes in this area as well as administrator activity, cybercriminals are faced with a much more difficult job when using stolen credentials to infiltrate a network.
Attempts at privilege escalation can be stopped in their tracks, and changes to system configurations can’t fly under the radar unnoticed.
The Takeaway
We know that cybercriminals are often part of high-tech, organized crime groups that relentlessly scope out victims and credentials to exploit for financial gain.
We know that most security breaches are perpetrated by outsiders trying to get in.
The endpoint is that way in.
The overwhelming takeaway from the data breach statistics over the past two years is:
Secure your endpoints.
For every endpoint you have that is uncontrolled, unmonitored, and unprotected, an attack surface exists to be exploited.
Planning Ahead with PAM
Privileged Access Management (PAM) is a form of endpoint security that does as the name suggests: manages who has privileged access within your organization.
But not all PAM solutions are created equal; a good one will go above and beyond.
Admin By Request is a cloud-based PAM solution that covers each of the points mentioned above, featuring extensive monitoring capabilities, real-time malware detection and user-friendly reporting, all accessible within the online user portal.
1. Be more diligent with monitoring devices.
For every endpoint that has Admin By Request deployed, data is collected and displayed within the software’s user portal; geographical location, elevated users, installed applications, local administrators, new computers, and other data and activity is monitored for each and every device and displayed within the Reports tab of the user portal.
Keeping track of as much user and device data as possible, and subsequently any unexpected changes in this data, ensures endpoint threat surfaces are minimized.
2. ‘Digital tether’
Admin By Request’s user portal is the heart of the software – the single location from which to access the Inventory, Auditlog, Settings, and Requests for elevation.
From here you can customize settings for endpoints and users, with the software’s mobile application ensuring you’re always connected to your endpoints and users, even while on the move.
Having this central vantage point from which to view and configure endpoints means the likelihood of a cybercriminal being able to exploit a single endpoint unnoticed is much lower.
3. A cloud-based future.
Cloud-based operating provides several advantages, both for productivity and cybersecurity reasons.
Admin By Request is a cloud-based software service, which can be deployed and set up for both small and large enterprises remotely, quickly, and easily.
The PAM software integrates with OPSWAT’s MetaDefender Cloud API to protect all endpoints from malware using more than 35 anti-virus engines – because a single, endpoint ant-virus solution doesn’t cut it against the advanced tactics employed by cybercriminals today.
MetaDefender scans files in real-time, flagging malicious files before they can do any harm to your endpoints and wider network.
4. Manage privileged access.
Admin By Request’s privileged access management capabilities are integral to keeping your endpoints and organization safe.
The less privileges a user has on their device, the less ability they have to make system wide changes that compromise security – and the safer your organization is.
Admin By Request revokes local administrator rights, while still allowing users to temporarily gain elevated access when they need it – but never by elevating the user.
Instead, the application gains elevated privileges while in use. That way, the user – and cybercriminals looking to exploit – never gain administrative access to the system.
While a user is running an application with privileged access, session information such as the user details, software installs, and executed programs, are logged within the Auditlog in the user portal, so you can access all necessary data in the case of a breach.
Conclusion
The number one lesson on cybersecurity for the past two years is to secure and protect your endpoints.
And although a new year doesn’t simply allow us to hit the reset button, we can start somewhat afresh with a clean slate and a new plan in place.
Part of that plan should be a comprehensive PAM solution that does more than just keep your local administrators in line.
Get started with Admin By Request today.







