
Documentation
Integrations > Microsoft Sentinel.
Add another layer of enterprise security with our latest integration: send Auditlog and Events data from your Admin Portal to your Microsoft Sentinel setup.
Ready to get started? Download the step-by-step guide at the button below.
Find the code for this integration at the following links:
Why Integrate Microsoft Sentinel?
Is there such a thing as too much security? Not in our books. And that’s why we offer a public REST API to our customers as part of their Admin By Request license: providing the ability to pull data into your own SIEM system for further analysis.
The latest SIEM we’ve built an integration for is Microsoft Sentinel – Microsoft’s “scalable, cloud-native, security information and event management (SIEM) and security orchestration, automation, and response (SOAR) solution”.
What the Integration Offers
With this integration, we’ve set up a hassle-free way to send Auditlog and Events data from your User Portal to Microsoft Sentinel using Azure Logic Apps. It’s quick, painless, and ensures you get the best of both worlds: comprehensive user data combined with Sentinel’s intelligent security analysis and threat detection capabilities.
How it Works
Microsoft Sentinel offers various ways to consume data from different sources. For this integration, we leverage the power of Azure Logic Apps to consume the Admin By Request Auditlog and Events APIs and forward each new entry to an Azure Log Analytics Workspace for further Sentinel consumption.
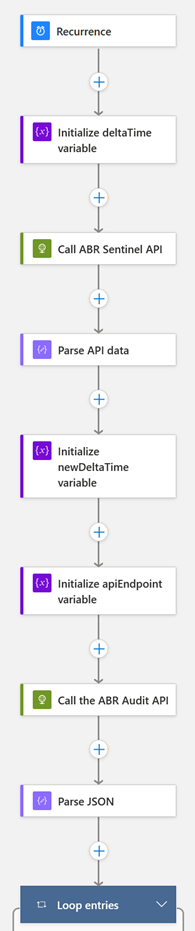
The Azure Logic App requires only a few simple changes before having you up and running with the appropriate data in your Sentinel setup:
- Set up the workspace
- Create an Azure Logic App
- Plug in the code
- Enter parameters
- Add some actions
- Run the app
You can then point your Sentinel setup to use the configured workspace as a data source.
Download the manual below for a step-by-step how-to guide:
Something Missing?
If you’ve identified a bug or have a suggestion for this integration, or another SIEM integration you’d like us to add, contact us here and we’ll see what we can do.
Code – Auditlog Data
{
"definition": {
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
"actions": {
"Call_ABR_Sentinel_API": {
"inputs": {
"body": {
"ApiKey": "@{parameters('ApiKey')}",
"Ticks": "@variables('deltaTime')"
},
"method": "POST",
"uri": "https://sentinel.adminbyrequest.com/Audit/SetDeltaTime"
},
"runAfter": {
"Initialize_deltaTime_variable": [
"Succeeded"
]
},
"type": "Http"
},
"Call_the_ABR_Audit_API": {
"inputs": {
"headers": {
"apikey": "@parameters('ApiKey')"
},
"method": "GET",
"uri": "https://dc1api.adminbyrequest.com/auditlog/delta?deltaTime=@{variables('newDeltaTime')}"
},
"runAfter": {
"Initialize_newDeltaTime_variable": [
"Succeeded"
]
},
"type": "Http"
},
"Initialize_deltaTime_variable": {
"inputs": {
"variables": [
{
"name": "deltaTime",
"type": "integer",
"value": "@ticks(utcNow())"
}
]
},
"runAfter": {},
"type": "InitializeVariable"
},
"Initialize_newDeltaTime_variable": {
"inputs": {
"variables": [
{
"name": "newDeltaTime",
"type": "integer",
"value": "@body('Call_ABR_Sentinel_API')"
}
]
},
"runAfter": {
"Call_ABR_Sentinel_API": [
"Succeeded"
]
},
"type": "InitializeVariable"
},
"Loop_entries": {
"actions": {},
"foreach": "@body('Parse_JSON')?['entries']",
"runAfter": {
"Parse_JSON": [
"Succeeded"
]
},
"type": "Foreach"
},
"Parse_JSON": {
"inputs": {
"content": "@body('Call_the_ABR_Audit_API')",
"schema": {
"properties": {
"entries": {
"items": {
"properties": {
"application": {
"properties": {
"file": {
"type": [
"string",
"null"
]
},
"name": {
"type": [
"string",
"null"
]
},
"path": {
"type": [
"string",
"null"
]
},
"preapproved": {
"type": "boolean"
},
"scanResult": {
"type": [
"string",
"null"
]
},
"scanResultCode": {
"type": "integer"
},
"sha256": {
"type": [
"string",
"null"
]
},
"threat": {},
"vendor": {
"type": [
"string",
"null"
]
},
"version": {
"type": [
"string",
"null"
]
},
"virustotalLink": {
"type": [
"string",
"null"
]
}
},
"type": "object"
},
"approvedBy": {
"type": [
"string",
"null"
]
},
"auditlogLink": {
"type": [
"string",
"null"
]
},
"computer": {
"properties": {
"make": {
"type": [
"string",
"null"
]
},
"model": {
"type": [
"string",
"null"
]
},
"name": {
"type": [
"string",
"null"
]
},
"platform": {
"type": [
"string",
"null"
]
},
"platformCode": {
"type": "integer"
}
},
"type": "object"
},
"deniedBy": {},
"deniedReason": {},
"elevatedApplications": {
"items": {
"properties": {
"file": {
"type": [
"string",
"null"
]
},
"name": {
"type": [
"string",
"null"
]
},
"path": {
"type": [
"string",
"null"
]
},
"scanResult": {
"type": [
"string",
"null"
]
},
"scanResultCode": {
"type": "integer"
},
"sha256": {
"type": [
"string",
"null"
]
},
"threat": {},
"vendor": {
"type": [
"string",
"null"
]
},
"version": {
"type": [
"string",
"null"
]
},
"virustotalLink": {
"type": [
"string",
"null"
]
}
},
"required": [
"name",
"path",
"file",
"version",
"vendor",
"sha256",
"scanResult",
"scanResultCode",
"threat",
"virustotalLink"
],
"type": "object"
},
"type": "array"
},
"endTime": {
"type": [
"string",
"null"
]
},
"endTimeUTC": {
"type": [
"string",
"null"
]
},
"id": {
"type": "integer"
},
"installs": {
"items": {
"properties": {
"application": {
"type": [
"string",
"null"
]
},
"vendor": {
"type": [
"string",
"null"
]
},
"version": {
"type": [
"string",
"null"
]
}
},
"required": [
"application",
"version",
"vendor"
],
"type": "object"
},
"type": "array"
},
"reason": {
"type": [
"string",
"null"
]
},
"requestTime": {
"type": [
"string",
"null"
]
},
"requestTimeUTC": {
"type": [
"string",
"null"
]
},
"responseTime": {
"type": [
"string",
"null"
]
},
"scanResults": {
"items": {
"properties": {
"engine": {
"type": [
"string",
"null"
]
},
"scanResult": {
"type": [
"string",
"null"
]
},
"scanResultCode": {
"type": "integer"
},
"threat": {}
},
"required": [
"scanResult",
"scanResultCode",
"engine",
"threat"
],
"type": "object"
},
"type": "array"
},
"settingsName": {
"type": [
"string",
"null"
]
},
"startTime": {
"type": [
"string",
"null"
]
},
"startTimeUTC": {
"type": [
"string",
"null"
]
},
"status": {
"type": [
"string",
"null"
]
},
"statusCode": {
"type": "integer"
},
"traceNo": {
"type": [
"string",
"null"
]
},
"type": {
"type": [
"string",
"null"
]
},
"typeCode": {
"type": "integer"
},
"uninstalls": {
"items": {
"properties": {
"application": {
"type": [
"string",
"null"
]
},
"vendor": {
"type": [
"string",
"null"
]
},
"version": {
"type": [
"string",
"null"
]
}
},
"required": [
"application",
"version",
"vendor"
],
"type": "object"
},
"type": "array"
},
"user": {
"properties": {
"account": {
"type": [
"string",
"null"
]
},
"email": {
"type": [
"string",
"null"
]
},
"fullName": {
"type": [
"string",
"null"
]
},
"phone": {
"type": [
"string",
"null"
]
}
},
"type": "object"
}
},
"required": [
"id",
"traceNo",
"settingsName",
"type",
"typeCode",
"status",
"statusCode",
"reason",
"approvedBy",
"deniedReason",
"deniedBy",
"requestTime",
"requestTimeUTC",
"startTime",
"startTimeUTC",
"endTime",
"endTimeUTC",
"responseTime",
"auditlogLink",
"user",
"computer",
"application",
"installs",
"uninstalls",
"elevatedApplications",
"scanResults"
],
"type": "object"
},
"type": "array"
},
"timeNow": {
"type": "integer"
}
},
"type": "object"
}
},
"runAfter": {
"Call_the_ABR_Audit_API": [
"Succeeded"
]
},
"type": "ParseJson"
}
},
"contentVersion": "1.0.0.0",
"outputs": {},
"parameters": {
"ApiKey": {
"defaultValue": "xxxxxx",
"type": "String"
},
"LogName": {
"defaultValue": "AdminByRequestLogs",
"type": "String"
}
},
"triggers": {
"Recurrence": {
"evaluatedRecurrence": {
"frequency": "Day",
"interval": 1,
"startTime": "2022-06-22T15:00:00Z"
},
"recurrence": {
"frequency": "Day",
"interval": 1,
"startTime": "2022-06-22T15:00:00Z"
},
"type": "Recurrence"
}
}
},
"parameters": {}
}
Code – Events Data
{
"definition": {
"$schema": "https://schema.management.azure.com/providers/Microsoft.Logic/schemas/2016-06-01/workflowdefinition.json#",
"actions": {
"Call_ABR_Sentinel_API": {
"inputs": {
"method": "GET",
"uri": "https://sentinel.adminbyrequest.com/Events/GetEventStartId?apiKey=@{parameters('ApiKey')}"
},
"runAfter": {},
"type": "Http"
},
"Call_the_ABR_Audit_API": {
"inputs": {
"headers": {
"apikey": "@parameters('ApiKey')"
},
"method": "GET",
"uri": "@{variables('apiEndpoint')}/events?startId=@{variables('startEventId')}&take=10000"
},
"runAfter": {
"Initialize_apiEndpoint_variable": [
"Succeeded"
]
},
"type": "Http"
},
"Get_latest_eventId": {
"inputs": {
"headers": {
"apikey": "@parameters('ApiKey')"
},
"method": "GET",
"uri": "@{variables('apiEndpoint')}/events?last=1"
},
"runAfter": {
"Parse_JSON": [
"Succeeded"
]
},
"type": "Http"
},
"Initialize_apiEndpoint_variable": {
"inputs": {
"variables": [
{
"name": "apiEndpoint",
"type": "string",
"value": "@body('Parse_API_data')?['publicApiUrl']"
}
]
},
"runAfter": {
"Initialize_startEventId_variable": [
"Succeeded"
]
},
"type": "InitializeVariable"
},
"Initialize_latest_event_variable": {
"inputs": {
"variables": [
{
"name": "latestEventId",
"type": "integer",
"value": "@body('Parse_Latest_Event_JSON')[0]['id']"
}
]
},
"runAfter": {
"Parse_Latest_Event_JSON": [
"Succeeded"
]
},
"type": "InitializeVariable"
},
"Initialize_startEventId_variable": {
"inputs": {
"variables": [
{
"name": "startEventId",
"type": "integer",
"value": "@body('Parse_API_data')?['eventId']"
}
]
},
"runAfter": {
"Parse_API_data": [
"Succeeded"
]
},
"type": "InitializeVariable"
},
"Loop_entries": {
"actions": {},
"foreach": "@body('Parse_JSON')",
"runAfter": {
"Set_latest_event_ID": [
"Succeeded"
]
},
"type": "Foreach"
},
"Parse_API_data": {
"inputs": {
"content": "@body('Call_ABR_Sentinel_API')",
"schema": {
"properties": {
"eventId": {
"type": "integer"
},
"publicApiUrl": {
"type": "string"
},
"success": {
"type": "boolean"
}
},
"type": "object"
}
},
"runAfter": {
"Call_ABR_Sentinel_API": [
"Succeeded"
]
},
"type": "ParseJson"
},
"Parse_JSON": {
"inputs": {
"content": "@body('Call_the_ABR_Audit_API')",
"schema": {
"items": {
"properties": {
"additionalData": {},
"alertAccount": {},
"application": {
"properties": {
"file": {},
"name": {},
"path": {},
"sha256": {},
"vendor": {},
"version": {}
},
"type": "object"
},
"auditLogURL": {},
"computerName": {
"type": "string"
},
"eventCode": {
"type": "integer"
},
"eventLevel": {
"type": "integer"
},
"eventText": {
"type": "string"
},
"eventTime": {
"type": "string"
},
"eventTimeUTC": {
"type": "string"
},
"id": {
"type": "integer"
},
"rollback": {
"type": "boolean"
},
"userAccount": {},
"userName": {}
},
"required": [
"id",
"eventCode",
"eventLevel",
"eventText",
"eventTime",
"eventTimeUTC",
"computerName",
"userAccount",
"userName",
"alertAccount",
"auditLogURL",
"rollback",
"additionalData",
"application"
],
"type": "object"
},
"type": "array"
}
},
"runAfter": {
"Call_the_ABR_Audit_API": [
"Succeeded"
]
},
"type": "ParseJson"
},
"Parse_Latest_Event_JSON": {
"inputs": {
"content": "@body('Get_latest_eventId')",
"schema": {
"items": {
"properties": {
"additionalData": {},
"alertAccount": {},
"application": {
"properties": {
"file": {},
"name": {},
"path": {},
"sha256": {},
"vendor": {},
"version": {}
},
"type": "object"
},
"auditLogURL": {},
"computerName": {
"type": "string"
},
"eventCode": {
"type": "integer"
},
"eventLevel": {
"type": "integer"
},
"eventText": {
"type": "string"
},
"eventTime": {
"type": "string"
},
"eventTimeUTC": {
"type": "string"
},
"id": {
"type": "integer"
},
"rollback": {
"type": "boolean"
},
"userAccount": {
"type": "string"
},
"userName": {}
},
"required": [
"id",
"eventCode",
"eventLevel",
"eventText",
"eventTime",
"eventTimeUTC",
"computerName",
"userAccount",
"userName",
"alertAccount",
"auditLogURL",
"rollback",
"additionalData",
"application"
],
"type": "object"
},
"type": "array"
}
},
"runAfter": {
"Get_latest_eventId": [
"Succeeded"
]
},
"type": "ParseJson"
},
"Set_latest_event_ID": {
"inputs": {
"body": {
"ApiKey": "@parameters('ApiKey')",
"EventStartId": "@variables('latestEventId')"
},
"method": "POST",
"uri": "https://sentinel.adminbyrequest.com/Events/SetEventStartId"
},
"runAfter": {
"Initialize_latest_event_variable": [
"Succeeded"
]
},
"type": "Http"
}
},
"contentVersion": "1.0.0.0",
"outputs": {},
"parameters": {
"ApiKey": {
"defaultValue": "xxx",
"type": "String"
},
"LogName": {
"defaultValue": "SentinelTest",
"type": "String"
}
},
"triggers": {
"Recurrence": {
"evaluatedRecurrence": {
"frequency": "Day",
"interval": 1,
"startTime": "2022-06-22T15:00:00Z"
},
"recurrence": {
"frequency": "Day",
"interval": 1,
"startTime": "2022-06-22T15:00:00Z"
},
"type": "Recurrence"
}
}
},
"parameters": {}
}



