Don’t Get Hooked: 10 Social Engineering Indicators
Spot these social engineering indicators before you get tricked. Discover 10 red flags attackers use to manipulate your actions and access sensitive data.
Spot these social engineering indicators before you get tricked. Discover 10 red flags attackers use to manipulate your actions and access sensitive data.
PAN-OS vulnerability CVE-2025-0108 showed how fast hackers strike. Learn key lessons in patching, privilege control, and layered cybersecurity defenses.
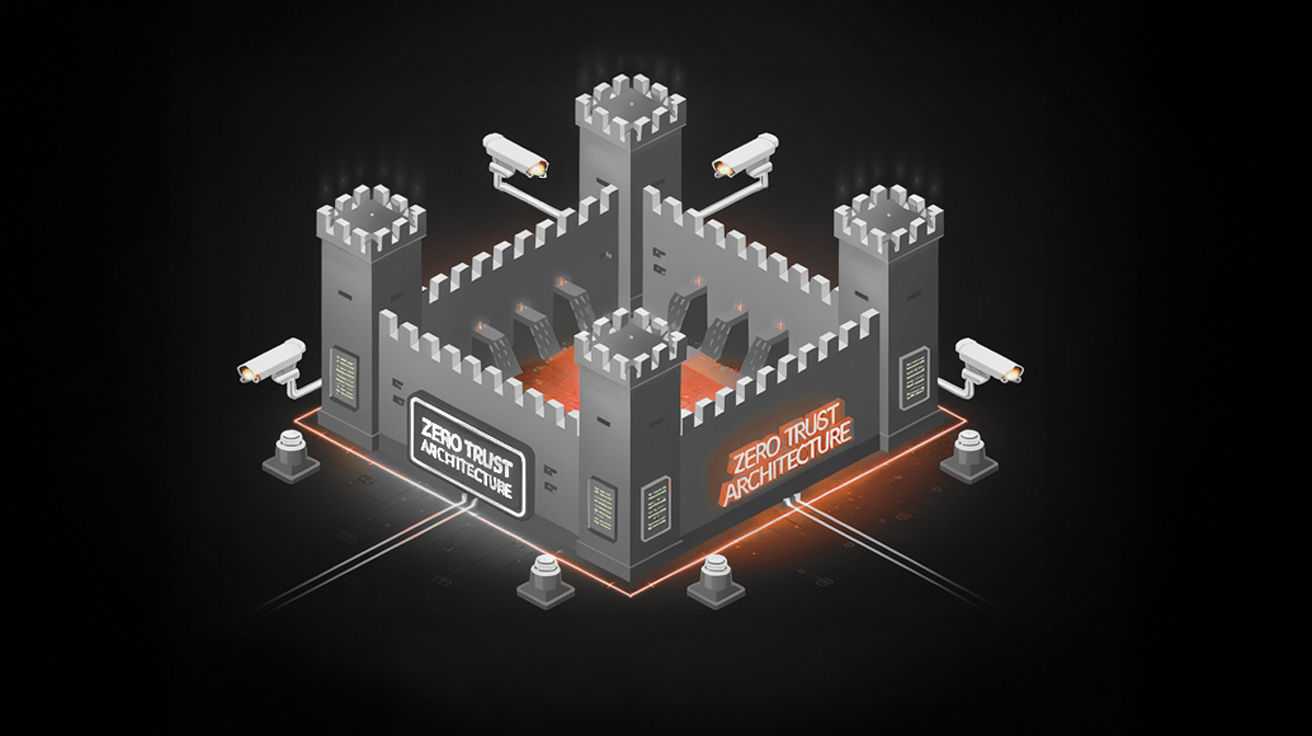
Find out how Zero Trust Architecture reduces risk, simplifies compliance, and protects your cloud environment with these 7 practical, proven benefits.
Strengthen RDP security with practical, real-world measures. Learn about the threats, best practices, and a more convenient way to keep remote work safe.
Back in February, Finastra announced a data breach that exposed customer info. Learn how it happened and what you can do to better protect your own data.
Enhance security and streamline IT with Endpoint Privilege Management (EPM). Reduce risks, ensure compliance, and optimize operations with least-privilege access.
Privileged Access Management controls & secures high-level accounts to prevent breaches, limit cyber threats, and ensure compliance. Here’s why it matters.
A recent Ransomware attack forced the Indian Multinational Technology giant to suspend several IT services. Here's the breakdown.
Learn how Privileged Access Management (PAM) secures sensitive data, reduces security risks, and ensures compliance by controlling privileged user access.
Find free remote desktop software for seamless access. Boost productivity with Admin By Request's secure, versatile solutions including a lifetime Free Plan.
A July 4th ransomware attack by SafePay crippled Ingram Micro systems. Explore the breach, its impact, and the rising threat of supply chain attacks.
When security feels like punishment, users push back. Learn how invisible security and smart UX make compliance effortless and effective.
Removing admin rights doesn’t mean losing productivity. See how just-in-time elevation keeps users moving while IT regains control and cuts tickets.