IBM’s 2021 Cost of a Data Breach Report is out – and it’s as disheartening as ever.
We’re ignoring the money side of things today and focusing on the time side, and the sad fact of the matter is… time is not on your side.
The report revealed the following:
- The average number of days it took for organizations to identify and contain a data breach in 2021 was 287.
- Of that 287, 212 was the average number of days it took solely for identification.
- A further 75 days were required on average to contain the breach after discovery.
- The average cost of a data breach with a lifecycle of over 200 days was $4.87 million USD.
- The data breach lifecycle took, on average, a week longer in 2021 than it did in 2020.
- Organizations that had more than a 50% remote-workforce took an extra 58 days to identify and contain the breach.
So, there are the numbers, in all their glory. To get a better shot at reducing them, let’s break them down.
Halt Hackers
A few years ago at the Microsoft Ignite conference – an annual event for developers and IT professionals – Raymond Comvalius did a presentation titled Halt Hackers, discussing the increasing sophistication of attacks and what you can do to protect yourself from them.
During the presentation, Raymond discussed a concept called The Attack Timeline: a breakdown spanning from the pre-attack planning stage, to the point of gaining entry, to when the attack is finally discovered.
The Attacker Decision Cycle
Halt Hackers likens the hacker decision cycle to the process of physically robbing of a bank.
Before any physical infiltration, there comes an decision cycle or ‘plan of attack’ by the bad guys – because one does not simply rob a bank on a whim (well, the successful bank robbers don’t anyway).
Cyber security infiltrations are no different.
The following four stages comprise the attack cycle:
- Observe – Hackers watch you. They observe what you do in your network.
- Orient – They tailor and adapt to the circumstances within your network, aligning themselves to the environment.
- Decide – They decide on the attack path.
- Act – They use this path to act and bring the entire organization down.
The Attack Timeline
The attacker decision cycle described above occurs during the Research and Preparation segment of the Attack Timeline below:
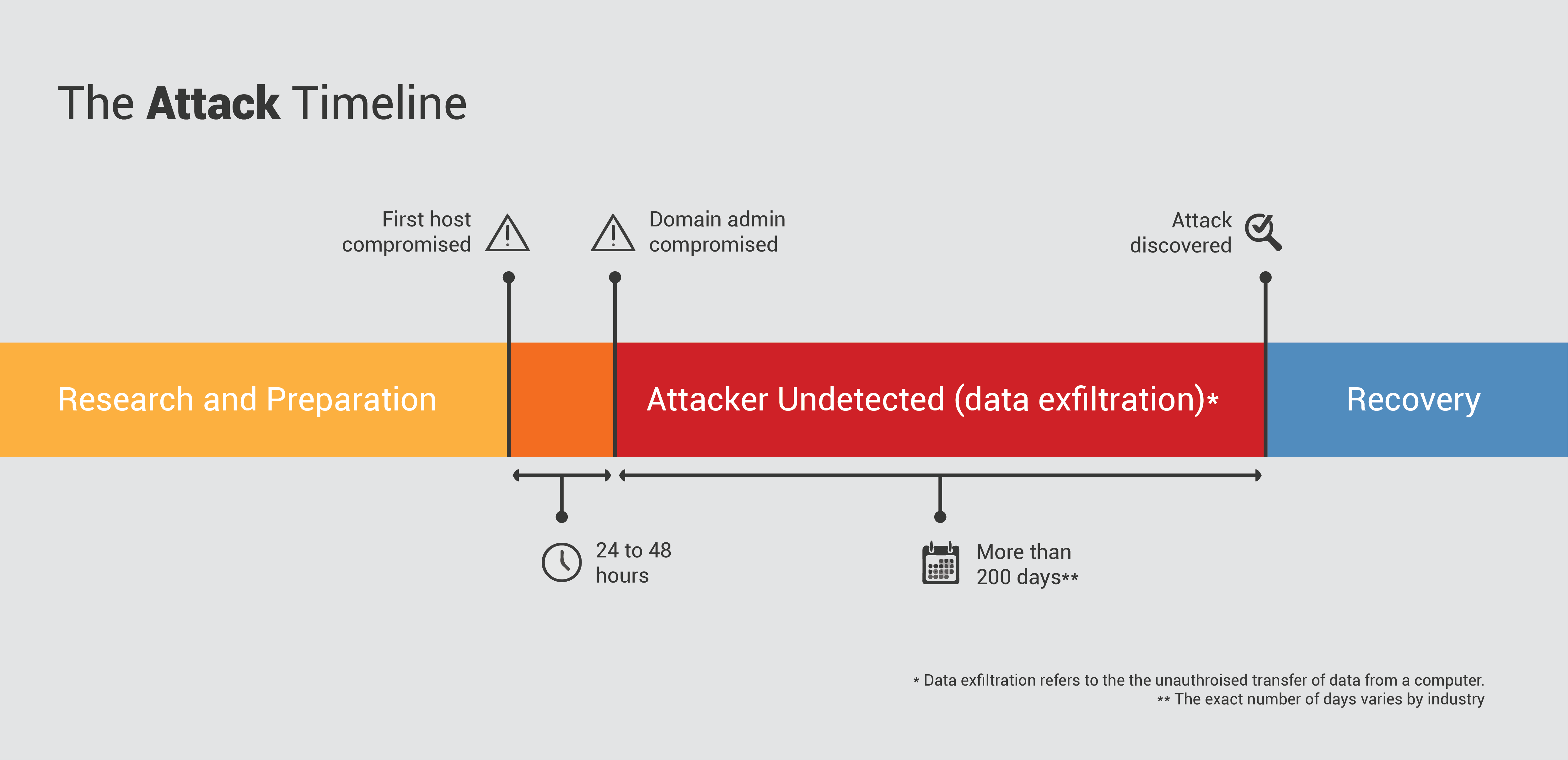
According to the timeline, once the Act stage of the attacker decision cycle ensues and the first host is compromised, the victim organization has 24 to 48 hours to detect an attack.
After this amount of time, hackers statistically have escalated to domain admin and the company is… [insert expletive of choice here].
Once domain admin has been compromised and attackers are inside your network, we know they can resist detection there for upwards of 200 days before you find them or find out that you’ve been hacked.
Halt Hacker’s makes a note of the following:
- Attacks are becoming increasingly sophisticated. Attack operators are targeting information on any device or service, exploiting any weaknesses they can find.
- Attackers often target Active Directory (AD), as gaining access to AD means attackers can cause damage on a much larger scale.
o Active Directory (AD) is a set of processes and services created by Microsoft for use on Windows operating systems; with one of these services being Domain Services (AD DS). A server running AD DS is also known as a domain controller. It is the center for domain management, essentially used to govern over devices on a network: allowing network admins to create and manage users and domains, access network resources and manage permissions.
- Current detection tools often miss attacks, meaning many go undetected until the damage has been done. Hackers enlist many techniques to help them stay hidden; one of these is clearing the Security Log – Windows Security Event ID 1102. Seeing this error can often mean a hacker has done this in an attempt to cover their tracks and the event needs to be investigated.
o The Security Log tracks security-related activity on an IT system, such as log ins or log outs and other security events specific to the system it is logging on.
- Response and recovery from a data breach once an attack is discovered is often costly and challenging, requiring advanced expertise and tools.
The Power of Protecting the Endpoint
Rather than spending large amounts of money on recovery after suffering from a breach, you ideally need to stop the breach from occurring in the first place – or at least detect it within the critical 24 to 48 hours that it takes for an attacker to gain domain admin access.
We’ve discussed attackers exploiting any vulnerability or weakness they can find: one of these is the end user – the ‘doorway’ that attackers often use to gain access to the entire IT network.
Protecting this doorway is achieved by protecting the local administrator – something you can do with the help of a Privileged Access Management (PAM) solution such as Admin By Request.
Privileged Access Management: Admin By Request
PAM allows you to manage, monitor and secure access to your companies’ network and everything on it.
A good PAM solution should protect the endpoint: by managing local administrators, reporting changes in the local administrator’s group, monitoring client event logs, and sending alerts to keep you in the know.
All of these mechanisms help to ensure that an attacker can’t escalate to domain admin and then roam undetected on your network for 200 days before being discovered.
Admin By Request’s PAM solution covers all bases.
- Admin By Request manages local administrators by smoothly and efficiently revoking administrator rights. Limiting the number of privileged accounts in your network lessens the attack surface, making it much harder for hackers to compromise a domain admin – particularly within 24 to 48 hours.
- Admin By Request reports changes in local administrator groups and displays the data within the software’s user portal, using graphics such as the following to illustrate the current status of admins:
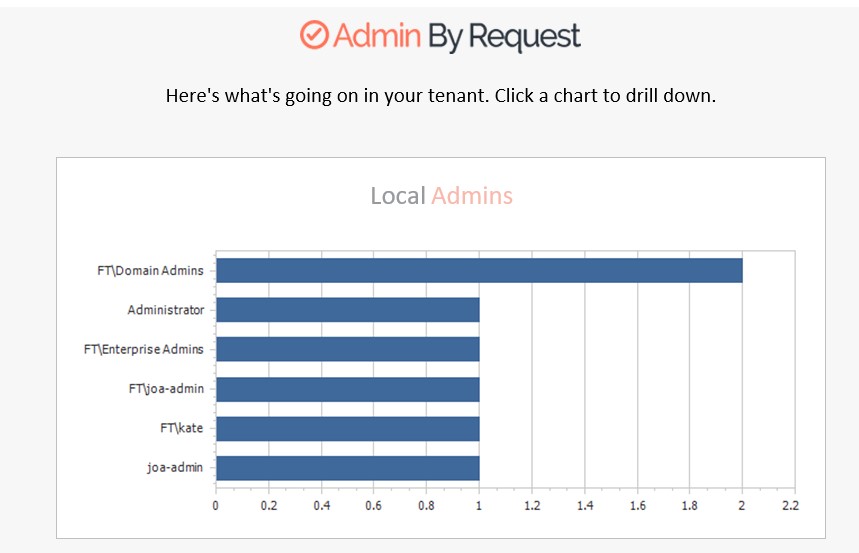
Changes to local admins or within local admin groups can indicate privilege escalation, which is the goal for many hackers attempting to infiltrate entire networks. Reporting tools such as the one above make it much harder for an attacker to successfully escalate from their first host – most likely a regular user – to a privileged account without being detected.
- The Admin By Request auditlog monitors what your users are doing when they run applications as administrator or have a timed session as administrator – two of the self-initiated methods provided by Admin By Request so that regular users can do what they need to do unhindered. The auditlog reports on user activity that could indicate attempts at privilege escalation. Requests for escalated privileges – and the logging that goes along with them – is available via the Admin By Request user portal and the IOS and Android compatible app.
- Admin By Request’s alerting keeps you a step ahead of hackers on the attack timeline. As well as sending you email alerts when malware is detected by Opswat’s MetaDefender Cloud – integrated into Admin By Request – this PAM solution also alerts you to the activities it’s monitored throughout the week in the form of a weekly digest. One of these is administrator groups (see the image above). The weekly digest also covers the following:
o User Elevations
o Elevated Applications
o User Installs
o User Requests
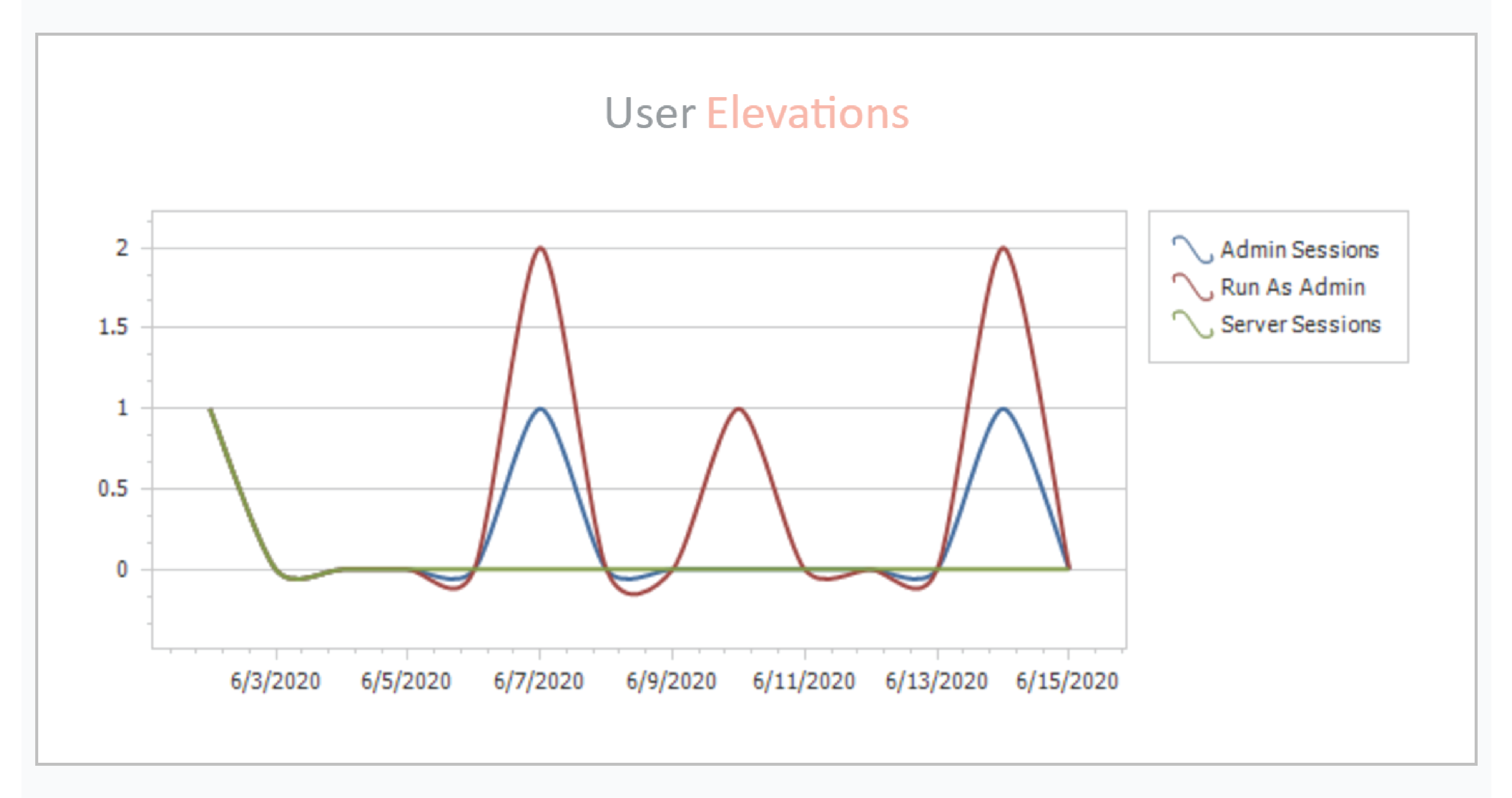
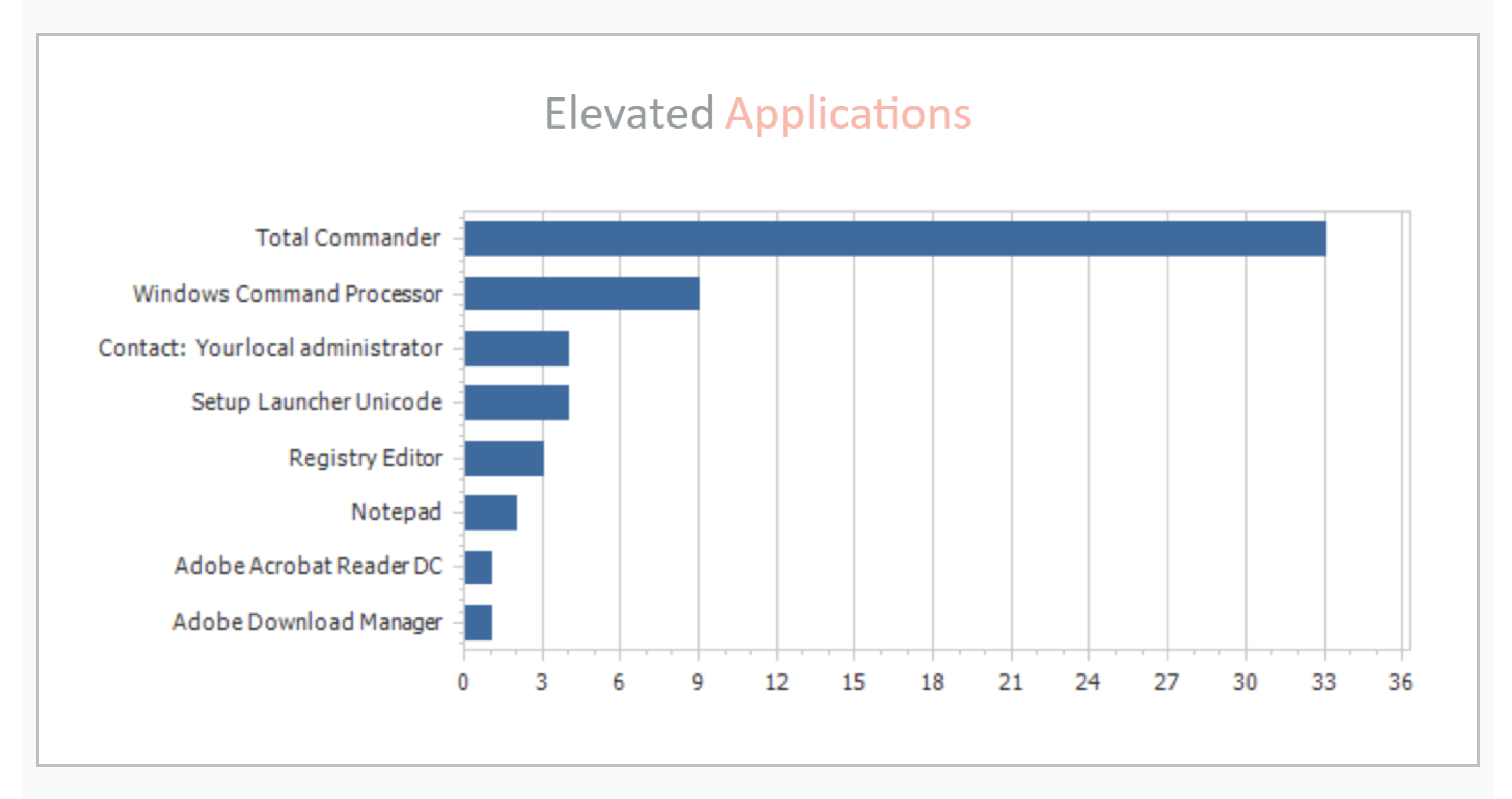
Constantly keeping you updated with a weekly breakdown leaves little wiggle room for hackers to move about freely without triggering investigation.
Conclusion
With a comprehensive PAM solution like Admin By Request managing, reporting, logging, and alerting, the attack timeline is halted long before domain admin can be compromised.
You can rest assured knowing the ability for an attacker to escalate up the ranks of privilege and remain undetected on your network for 212 days is practically impossible.
Many thanks to Raymond Comvalius and Erdal Ozkaya for their work on Halt Hackers, and the team at IBM – the inspiration for this blog.