There’s a new outlaw in town – but you won’t catch this guy with a heroic band of Merry Men.
Instead of stealing from the rich and giving to the poor, this aptly named piece of ransomware exploits a privilege escalation vulnerability in a kernel driver to infiltrate the network, encrypting files and demanding to be paid within four days – with the ransom increasing by $10,000 every day that it is not paid.
Out of the Forest and into the Network
A kernel manages computer operations and is essentially the core of the operating system. Gaining kernel control means gaining control of everything in the system.
RobbinHood ransomware is as mischievous as its namesake, gaining access to the kernel under the guise of a legitimate driver.
RobbinHood ransomware uses this to its advantage; instead of hunting for existing vulnerabilities within a network, it uses an old but legitimate Windows kernel driver from Gigabyte to ‘bring its own bug’ into the system.
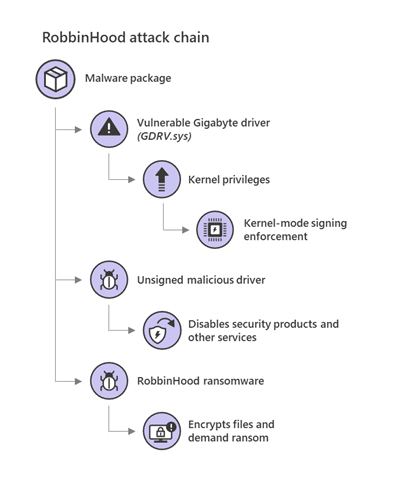
The malware consists of several files embedded in executable STEEL.EXE. Here’s an overview of the attack plan based on a research report from SophosLabs:
1. STEEL.EXE is extracted and plants file ROBNR.EXE onto the disk, which then installs the legitimate Gigabyte driver (GDRV.SYS) along with the malicious driver (RBNL.SYS).
- In order to be loaded into Windows 64-bit computers, drivers must be legitimate: signed by both Microsoft and the driver manufacturer. Windows recognises legitimate drivers by means of a driver signature enforcement process, and it therefore allows the GDRV.SYS to be installed.
2. Once installed, the GDRV.SYS is able to temporarily disable the driver signature enforcement mechanism due to a vulnerability that allows the driver to read and write to any part of the computer memory. With signature enforcement disabled, the malicious driver can then be loaded into kernel space.
3. Once the malicious driver is up and running, the ROBNR.EXE process exits and the PLIST.TXT file (a list of all applications to kill, often tailored to the target network), is processed. The malicious driver begins terminating security processes and deleting associated files on the list, using various deletion methods run consecutively.
4. When the STEEL.EXE has completed this process, it exits, and RobbinHood can encrypt network files unimpeded by security software.
The following image from a Windows Security blog illustrates the process:
Just in Time to Stop (and Audit) the Robbery
In the case of RobbinHood ransomware, privilege escalation is the steppingstone to the main attack; in order to install its malicious driver, it first needs elevated powers. This can start by gaining access to an already privileged account, or by accessing a less-privileged account and ascending the ranks (vertical privilege escalation) to the necessary level from which point the main goal can be achieved.
If you can prevent the surface area of attack by managing privileged users, and promptly detect attempts (or even success) at privilege escalation, you have a much better chance at stopping the ‘main event’ from eventuating. Doing this essentially removes the privileged-account foothold RobbinHood needs to deploy and run STEEL.EXE.
As a Privileged Access Management (PAM) system, Admin By Request does just that by limiting access rights of users.
Admin By Request adopts:
- The principle of least privilege (POLP) – giving user accounts and administrators only the rights they need to successfully do their jobs, and
- Just-in-time (JIT) elevation – only elevating privileges when and where they are absolutely necessary.
In every business’ computer network, there will be accounts and users that require higher privileges than others. But that does not have to mean giving some accounts privileged access and free rein all the time.
With Admin By Request’s Sub Settings, you can implement POLP by creating different access rules for specialised users and groups, depending on their needs. This means you can impose strict access controls for all but your two IT techs if you so choose, lessening the potential for malware like RobbinHood to gain access to an already privileged account.
JIT elevation safeguards are in place with Admin By Request providing users with four ways to perform tasks that require elevated privileges.
Three of these four methods require the user to request permission or obtain a PIN in order to gain administrator access – with Admin By Request’s auditlog recording and displaying all administrator activity that takes place during these requests.
Auditing user activity in this way can prevent ransomware attacks like RobbinHood (in which escalation is instrumental to staging the attack), as it allows you to detect possible privilege escalation as it occurs and take appropriate action.
To have the power to install system resources such as drivers (which RobbinHood ransomware relies on to perform encryption unhindered), a user would need full local admin rights of their system.
In Admin By Request, this would require the user to make a Full Session Elevation request. Again, gaining this type of access could require a reason and/or approval (depending on your settings in Admin By Request), and all installs and uninstalls are recorded with the details of the elevated session in the auditlog. This makes it a much harder task to climb up the ranks of privilege unnoticed.
Disrupting just one of RobbinHood ransomware’s many processes can thwart its plan entirely – removing the foothold of privileged accounts and privilege escalation with Admin By Request does just that.
You Need More than One Sheriff to Stop RobbinHood
There is a operation in RobbinHood’s execution that runs multiple deletion-processes sequentially to ensure everything on its PLIST.TXT list is deleted. Better to be safe than sorry, right?
To beat this ransomware at its own game, you need to take a leaf out of Sherwood Forest.
Admin By Request does this by integrating a PAM solution with Opswat MetaDefender’s multi-engine malware scanning tool, the MetaDefender Cloud.
This security tool scans files with more than 35 anti-malware scanning engines. To give you an idea of how effective this makes Admin By Request at keeping your system safe from malware, here are some numbers from Opswat’s Detection Efficacy Overview:
- 4 anti-malware engines detect 62.80% of the top 10,000 searched for threats from the MetaDefender Cloud database
- 12 anti-malware engines detect 90.53%
- 20 anti-malware engines detect 98.69%
- The MetaDefender Cloud detects 99.02%
That raises malware detection rates to almost 100%.
Conclusion
Like RobbinHood, today’s ransomware attacks use a range of tactics and often need to find success at every step to achieve their goal. The best way to combat this is to disrupt as many parts of the attack chain as possible.
Admin By Request’s PAM solution, combined with an anti-malware security tool that employs multiple scanning engines, leaves no leaf unturned.