Long story short? You’re not as worried as you should be.
Comfort: 1, Security: 0
When it comes to the far-reaching effects of Covid-19, it would seem there is misalignment between the likelihood of Remote Working Cyber Attacks being a major contributor to the global fallout, versus how concerned people are about them.
As the global pandemic continues to force governments to order lockdowns, close workplaces and impose social distancing rules, working from home has become the widely accepted way to operate for many businesses – and that fact is unlikely to change within the next few years.
But while it’s all very well for you and I to roll out of bed, put a shirt on over our PJ’s, slide into some slippers and have a work meeting from the cosiness of our own living rooms, gaining comfort in one area almost always means it’s been traded up in another.
In the case of working from home, comfort replaces cyber security – and that’s a problem.
Particularly when statistics show how little people think it is.
Drop Everything and Go Remote. Literally.
The migration to remote working has been put into action among organisations at an increasing rate over the years as technology has advanced and the possibilities to do so have arisen.
What Covid-19 has done is forced this change to happen much more abruptly than it would have minus-pandemic, leading to the hasty uprooting of the workforce from a central place to various remote locations, which in turn has lead to disorganisation among the workforce and sudden security holes in the IT network.
A report published in June by VMware Carbon Black revealed the following:
- 85% of chief technology, information and security officers did not believe that their workforce had been adequately equipped to work from home.
- 28% said “severe and significant” security gaps were the reasons behind this belief.
As unsettling as these percentages are, we can hardly be surprised.
You know how in horror movies, as soon as the characters split up, they start getting picked off one by one? Yeah. It’s a thing.
With the abrupt move to working from home, 25,000 secure endpoints at a single location can turn into 25,000 insecure devices spread far and wide with little to none of the protection they were afforded within the office.
Company-wide firewalls, VPNs, blacklisted IP addresses, data encryption, antivirus software and other security measures and policies are now gone as workers switch to using inadequately protected personal devices, potentially on insecure Wi-Fi networks.
A workforce using personal devices are more likely to partake in risky activity that they usually wouldn’t while working at the office – activity that could impact their entire organisation; but because they’re remote, visibility of what activity they’re doing is limited or gone altogether.
“A Chain is Only as Strong as its Weakest Link”
As the saying goes.
In this case, that translates to: one weakly-guarded device in the home office that has access to the company network is all it takes for a cyber attack to compromise the entire organisation.
Cyber criminals are well aware of this, which is why Remote Working Cyber Attacks have risen throughout the scramble to secure remote access points during the shift to working from home.
The VMware Black Carbon report found the following of the past 12 months:
- 90% of security professionals say they have had an increase in number of attacks faced.
- 80% of security professionals say attack-sophistication has increased.
- 94% of organisations worldwide have suffered a data breach.
It’s clear that cyber attacks are on the rise as the number of easy targets and weak points increase, so how much of a threat are they in the grand scheme of risks, post-pandemic?
The Greater the Risk, the Greater the Reward Risk
According to an analysis done by the Visual Capitalist, Remote Working Cyber Attack threat makes it into the top 9 most likely risks post-Covid-19.
The article, “What’s At Risk: An 18-Month View of a Post-COVID World”, takes data submitted by a large number of risk analysts and compiled in a World Economic Forum report and displays it visually in the infographic below:
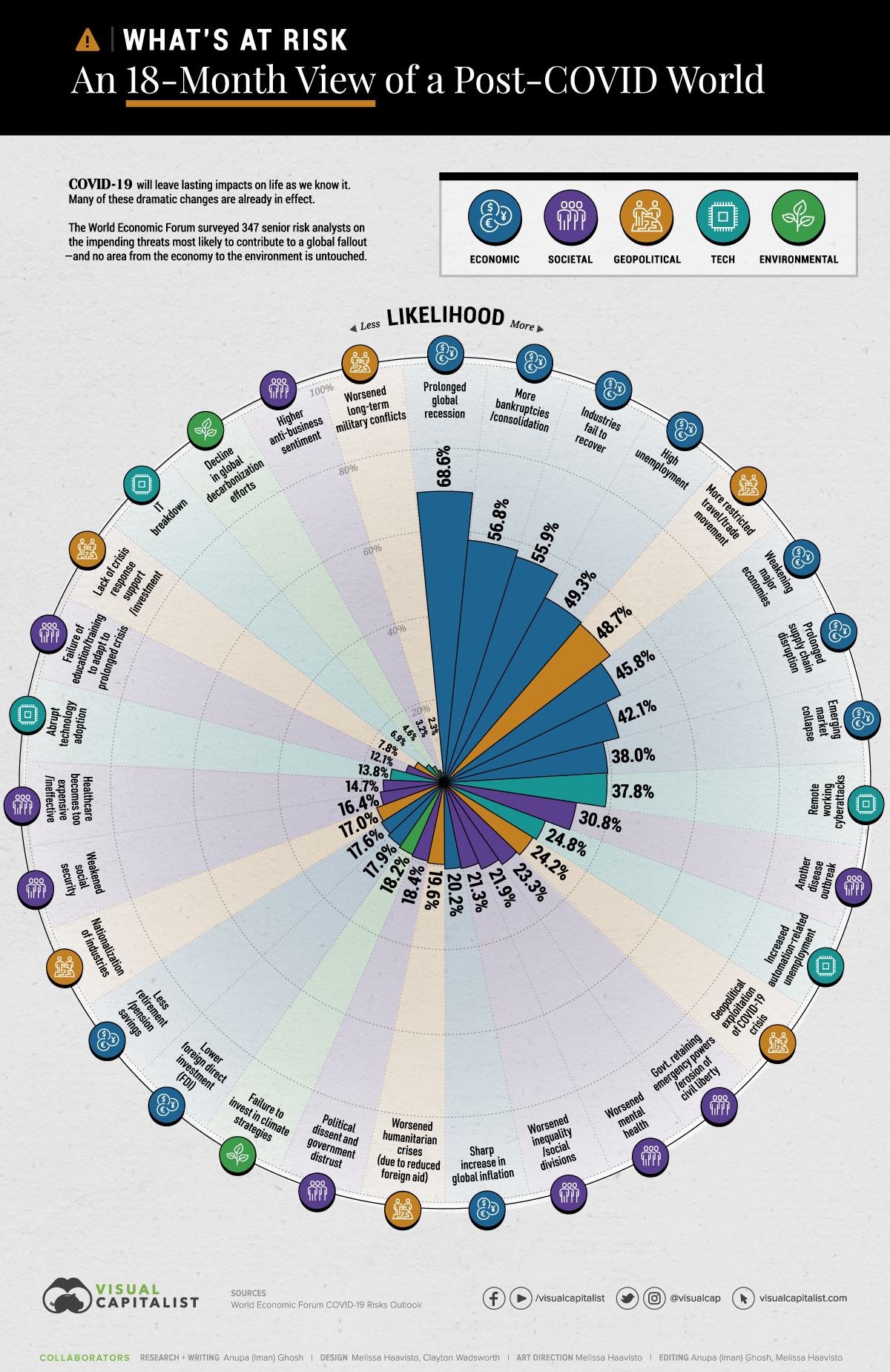
The infographic highlights the 31 biggest risks and their likelihood percentage within the next 18 months.
The risks are categorised into the following five areas:
- Economic
- Societal
- Geopolitical
- Tech
- Environmental
Of the four tech risks identified within the data set, Remote Working Cyber Attacks takes the number one spot with a likelihood of 37.8%.
That’s a significant jump ahead of the next tech threat identified: Increased Automation-related Unemployment, which sits at 24.8% likelihood, and is miles ahead of the next two tech threats: Abrupt Technology Adoption and IT Breakdown, which sit at 13.8% and 6.9%, respectively.
The scary fact is, the threat of Remote Working Cyber Attacks is great enough that it warrants a spot in the top 10 alongside the ‘big dogs’ of risks, so to speak: Prolonged Global Recession, High Unemployment, More Restricted Travel / Trade Movement and Industries Fail(ing) to Recover, among others.
Even scarier? People tend to drop this risk from the pool of ‘big dogs’ when it comes to their top concerns.
Post-Covid Priorities Are All Out of Whack
The Visual Capitalist gathered further data on how big of a concern these same risk analysts believed each risk was for the world:
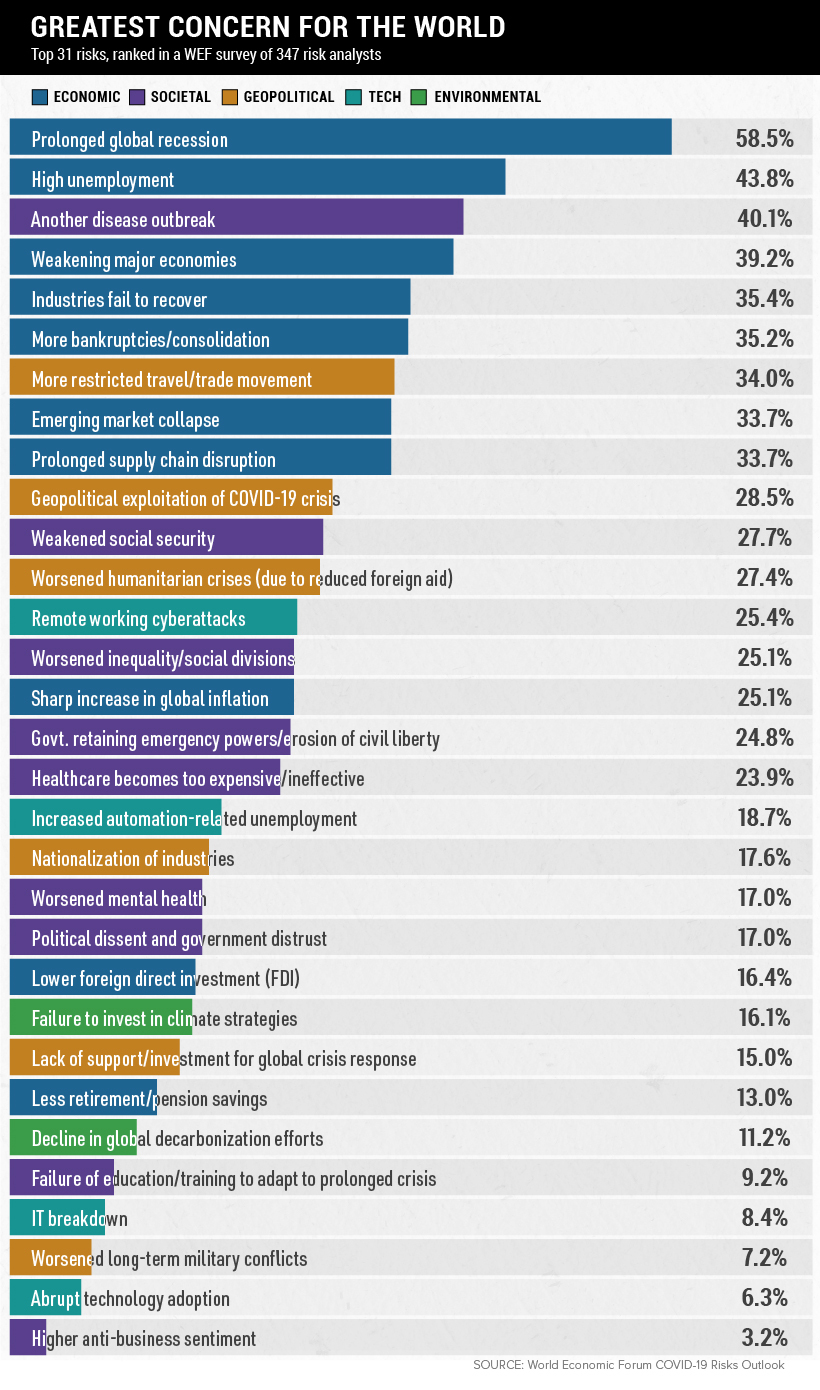
The findings show that all top 10 risks – bar one – have retained their places in the top 10 as concerns, albeit in a slightly different order.
The single threat that was considered a top 10 risk that didn’t make the cut this time around is our top tech risk: Remote Working Cyber Attacks, which now sits at 25.4% and 13th place when it comes to concern.
Essentially this means that although Remote Working Cyber Attacks are 37.8% likely to leave an impact on the world as we know it post-Covid, they are only seen as a 25.4% concern, with a 12.4% disparity.
When Disparity Becomes a Danger
This disparity in the actual threat versus how much it is perceived to be a threat, is a big problem.
It means that people working from home are unlikely to implement the proper security measures needed to protect themselves, their devices and subsequently, the data and networks they have remote access to from potential cyber attacks and data breaches.
In turn, organisations moving their workforce to remote locations are unlikely to take appropriate action to prevent Remote Working Cyber Attacks before they happen, because this risk is not seen as a big enough concern.
The fact of the matter is that you should be taking this threat seriously; ensuring that all potential holes that open up when your workforce goes remote are not only covered, but airtight.
Protect with PAM
A good way to ensure all of your endpoints are protected is by deploying a Privileged Access Management (PAM) solution to each and every remote endpoint.
PAM refers to the strategy of gaining full control and visibility of user-access to critical parts of the IT system and what they do when they have privileged access, so that data breaches and abuse of privilege can be prevented or audited in the case of occurrence.
PAM solutions do this by only allowing elevated privileges precisely when and where users need them and giving users only the minimum privileges required to perform their function in the workplace.
These techniques are known as Just-in-Time elevation (JIT) and the Principle of Least Privilege (POLP).
Admin By Request is a PAM solution that incorporates OPSWAT’s MetaDefender Cloud to ensure that hackers:
a) Can’t gain administrator access to endpoints without permission, therefore cannot undertake processes required to infiltrate your network, and
b) Can’t get past MetaDefender’s 35+ anti-malware engines that scan all files run as administrator, and prevent files flagged as malicious from being run on your endpoints and causing potential damage to your wider organisation.
Admin By Request, developed by the aptly named FastTrack Software, enables organisations to quickly and effectively manage privileged access and ensure the remote workforce is safe by:
1. Being easy to deploy on remote endpoints
Admin By Request makes ease of deployment a top priority. Requiring no AD configuration, the 3.5MB MSI installer takes minutes to get up and running on endpoints in the home.
2. Patching up any security holes opened up as a result of the move
Admin By Request ensures your network, systems and data stays safe from Remote Working Cyber Attacks by managing who can get higher-level access, what access they can get, and when they can get it.
All remote users can be managed from within the Admin By Request user portal. Admin By Request’s Settings and Sub-settings allow user groups to be created with different levels of admin privileges depending on their needs.
With Admin By Request, you get full visibility of what your users are getting up to when they’re operating with administrator privileges, with the user portal displaying Inventory collected for each device, an Auditlog of all elevated activity and Reports which sum up and display the important bits.
OPSWAT’s MetaDefender Cloud anti-malware solution is the ever-present second layer of protection, flagging down malicious files as they’re encountered – which is likely to continue happening at an increasing rate, particularly in a post-pandemic world where working from home is the norm.
Admin By Request also utilizes a sandbox environment to further ensure your endpoints – and company bits and pieces that these endpoints can access – stay safe.
3. Still giving remote workers the privileged access they need to stay productive
Remote access to company networks can be granted to home-workers without compromising security, but while maintaining productivity.
Remote users simply request administrator privileges to run applications as administrator or to have a timed session with administrator access. This allows remote users to stay productive: they can gain elevated privileges when and where they need them, but at the same time it keeps your network, systems and data safe by preventing unauthorised or unsecure actions that could affect the rest of the organisation.
You have the option to approve or deny user requests for elevated privileges within the online user portal Request page or by using the mobile app, with the simple push of a button. And the biggest advantage of the mobile app? Requests can be approved or denied while you’re stuck at home too, in the middle of attending to the teenage tantrums and tripping over the Harry Potter Lego scattered on the living room floor.
Get more details here about how Admin By Request can help make the remote workforce safe by managing admin rights.
Summary
The statistics show that you’re not as worried about Remote Working Cyber Attacks as you should be.
A post-Covid-19 world is going to be hard enough to navigate without the extra stress of a network-wide cyber attack resulting from an inadequately secured remote workforce.
PAM ensures that you’ll be fully-equipped to work from home and that your home-workers have access to the data and systems they need without compromising security.
Take the risk seriously and protect all your working-from-home endpoints before they become a concern with Admin By Request.