Over 100 Romanian Hospitals Hit with Ransomware Attack
In a targeted onslaught, orchestrated cybercriminals launched a ransomware attack on 100 hospitals across Romania. The sophisticated strike was aimed at the Hipocrate Information System (HIS) –a multipurpose healthcare management platform utilized by hospitals nationwide. It’s believed that all affected hospitals fell victim to the ransomware through the HIS.
Overnight on February 11th 2024, the attackers infiltrated the HIS production servers, swiftly encrypting files and databases vital for hospital functions. The scale of the crisis emerged the next morning: more than 100 hospitals have either had their files encrypted (26 as of February 16th) or have preemptively disconnected systems to prevent further contagion (79). The count of impacted healthcare facilities now exceeds the number of NHS trusts affected by the WannaCry ransomware attack in 2017.
Despite the challenges, a positive development arose: the majority of hospitals had recent data backups, reducing the risk of permanent data loss. The ransom demand – 3.5 BTC (approximately €157,000) – underscored the financial motive behind the attack, however no group has yet come forward to claim responsibility, nor has the ransom been paid.
In the chaos, medical professionals reverted to archaic methods, relying on pen and paper to maintain patient records and prescriptions. The impact of the attack extended beyond Romania’s borders, sounding an alarm for healthcare institutions worldwide – because attacks on the vulnerable healthcare industry are on the rise, and showing no signs of slowing.
Healthcare Sensitive Data an Attractive Target
In recent years, the healthcare industry has increasingly become a prime target for cybercriminals, with a notable surge in attacks reported across various sectors of healthcare organizations. In 20223, Hospitals and Healthcare made it to the top 5 targeted industries, just below Retail:
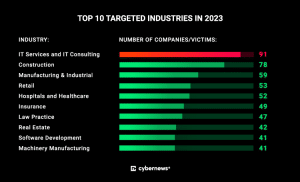
The motives behind these attacks range from financial gain to political agendas, with cybercriminals exploiting vulnerabilities in healthcare systems for various malicious purposes.
One key reason for the heightened targeting of this sector is the vast amount of sensitive data it holds. Patient medical records, billing information, and personal data are highly sought after on the dark web, fetching high prices on underground marketplaces. The critical nature of healthcare services means that any disruption or compromise of systems can have dire consequences, including jeopardizing patient care, compromising patient safety, and in some cases – costing lives. Therefore, any ransom attacks or demands are going to be met with desperation and taken very seriously.
The COVID-19 pandemic further exacerbated these vulnerabilities as healthcare systems worldwide faced unprecedented challenges, including rapid adoption of telehealth services, increased reliance on digital platforms, and stretched resources. Cybercriminals capitalized on these disruptions, launching targeted attacks aimed at exploiting weaknesses in hastily implemented digital infrastructures and preying on the chaos and uncertainty surrounding the pandemic.
Moreover, regulatory requirements such as HIPAA (Health Insurance Portability and Accountability Act) impose stringent data security and privacy standards on healthcare organizations, making them attractive targets for cybercriminals seeking to exploit compliance gaps and weaknesses in cybersecurity defenses.
Steps for Resilience
To protect themselves against the growing threat landscape, healthcare organizations must prioritize cybersecurity and adopt a proactive approach to risk management.
- User Training and Awareness: Educate hospital staff about the risks of ransomware and the importance of cybersecurity best practices. Training programs should cover topics such as identifying phishing emails, avoiding malicious links and attachments, and reporting suspicious activities promptly.
- Collaboration and Sharing: Actively engage in collaborative efforts within the industry to combat evolving threats. This involves participating in threat intelligence sharing initiatives, collaborating with industry peers, government agencies, and cybersecurity experts, and exchanging insights and best practices for effective cyber defense.
- Network Monitoring and Intrusion Detection: Employ network monitoring tools and intrusion detection systems (IDS) to detect unusual network activity and behavior indicative of ransomware infections. These tools can provide early warning signs of an attack, allowing hospitals to respond swiftly and contain the threat.
- Data Backup and Recovery: Implement robust data backup and recovery solutions to create regular backups of critical data and systems. In the event of a ransomware attack, hospitals can restore encrypted files from backups without paying the ransom, minimizing downtime and data loss.
- Patch Management: Utilize patch management software to ensure that operating systems, applications, and firmware are up to date with the latest security patches. Regular patching closes known vulnerabilities that ransomware may exploit to infiltrate hospital networks.
- Endpoint Protection: Deploying advanced antivirus software with real-time threat detection capabilities helps hospitals detect and block ransomware before it can infect endpoints. These solutions should include features like behavior-based analysis, heuristic scanning, and sandboxing to identify and quarantine malicious files.
- Privileged Access Management (PAM): Implementing PAM solutions allows hospitals to control and monitor access to critical systems and sensitive data. By enforcing least privilege access policies, hospitals can limit the privileges of users and applications to only what is necessary for their roles, reducing the attack surface for ransomware.
Simple Solutions in Complicated Environments
In the wake of increasing cyber threats targeting the healthcare sector, comprehensive solutions like Admin By Request Privileged Access Management (PAM) offers features specifically designed to mitigate the risks highlighted by recent attacks, as well as address the security and compliance challenges faced by hospitals and healthcare organizations.
Granular Control over Administrative Privileges
Admin By Request provides precise management of administrative privileges, preventing unauthorized access to critical systems and data. This feature enhances identity and asset management, ensuring only authorized personnel access sensitive healthcare information, thereby mitigating the risk of ransomware attacks and data breaches.
Self-Service Access Management
Admin By Request provides a self-service access management solution that doesn’t hinder productivity. In a hospital setting where swift access to critical systems and assets is paramount, this feature allows users to obtain the access they need safely. By empowering users to manage their access while remaining protected from external threats, Admin By Request enhances operational efficiency and security simultaneously.
Compliance Assurance with Audit Trail and Session Recording
Admin By Request’s audit trail and session recording capabilities are instrumental in maintaining compliance with regulations like HIPAA. By offering comprehensive visibility into privileged user activities, Admin By Request assists healthcare organizations in demonstrating compliance and facilitating forensic analysis during security incidents.
Antimalware Functionality for Enhanced Endpoint Security
Admin By Request PAM offers antimalware functionality, scanning files using multiple engines, quarantining them, and triggering alerts upon malware detection. This proactive approach enhances endpoint security, further fortifying healthcare organizations against ransomware attacks and other cyber threats.
Seamless Integration with Existing Workflows
Admin By Request seamlessly integrates with existing workflows, offering significant benefits to healthcare institutions that are often under pressure and stretched thin. By minimizing disruptions to daily operations, this solution enables hospitals to enhance their security posture without imposing additional burdens on their IT teams or clinical staff.
Try it Free
If you’re seeking an security solution to solve an array of challenges faced by the healthcare industry in an increasingly hostile digital landscape, try Admin By Request today. It’s available on a free lifetime plan at the link below for up to 25 Workstation endpoints, and 10 server endpoints.
Sources:
- https://media.cybernews.com/2024/01/top-10-targeted-industries-2023.png
- https://www.forbes.com/sites/davidchou/2023/12/29/2024-healthcare-cybersecurity-mastering-the-fundamentals/?sh=30391e8a4fdb
- https://www.himss.org/news/2024-predictions-healthcare-cybersecurity
- https://www.msn.com/en-us/news/technology/romanian-hospital-ransomware-crisis-attributed-to-third-party-breach/ar-BB1igXCK






